A Case for CTEM: Why Now Is the Time to Act
Zero in on the threats that matter most—and leave reactive firefighting behind—with CTEM.
The number of global vulnerabilities in 2025 set a record by exceeding 48,185 CVEs, with CVE volume surging from 2024 by
21%
Breaches frequently exploit unaddressed vulnerabilities, costing a global average of
4.1 million
Standing still is no longer an option.
Organizations need a proactive, structured approach — and that’s where Continuous Threat Exposure Management (CTEM) comes in.
CTEM isn’t just a buzzword
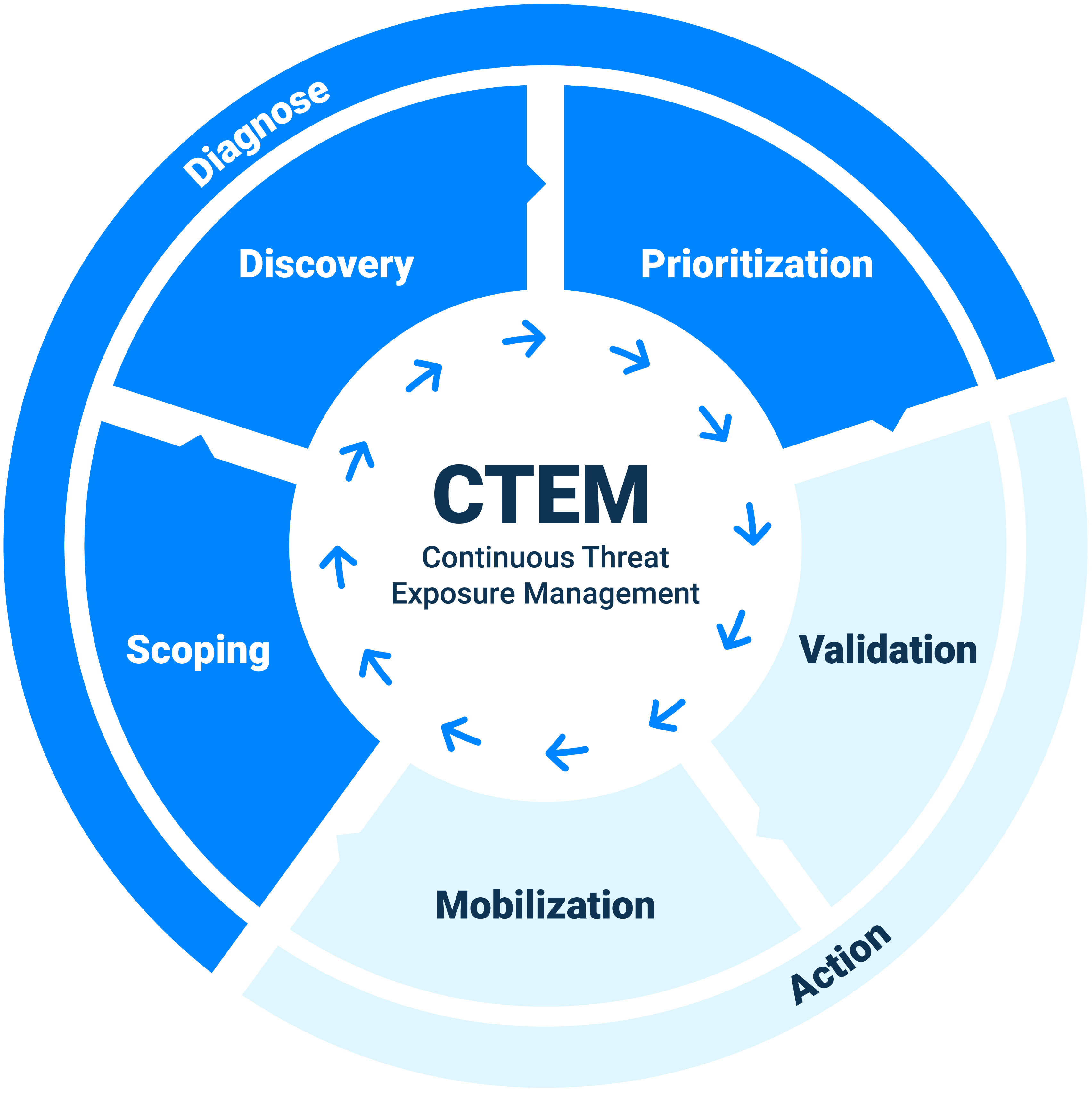
It’s a programmatic solution built around 5 core steps:
Scoping – Define what to test and protect
Discovery – Identify assets and exposures
Prioritization – Focus on what matters most
Validation – Simulate real-world threats
Mobilization – Drive remediation and action

Get limited-time Complimentary CTEM Fast Track Assessment
Aligned with our first-to-market CTEM Maturity Model.
Evaluate your current CTEM maturity
Identify gaps and next steps to strengthen your program




