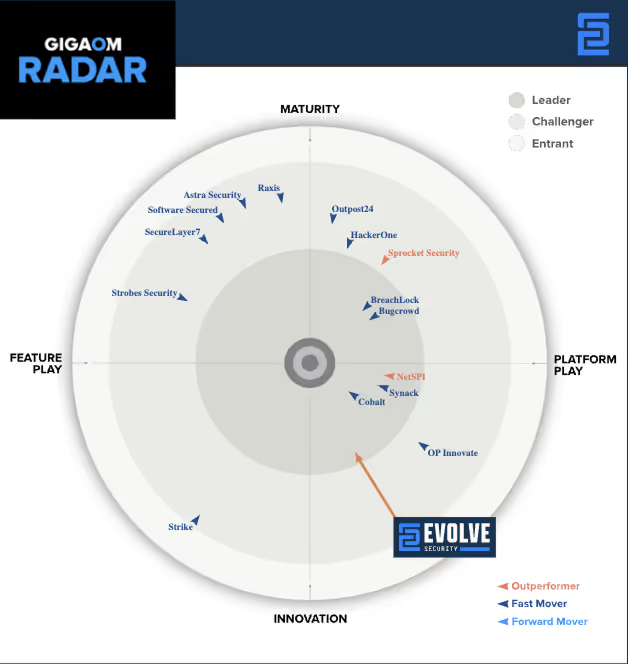
Managing Risk with ASM whitepaper
Your threat landscape is more dynamic than ever, spanning cloud, subsidiaries, and unknown assets. Attackers exploit unseen exposure. Learn how Attack Surface Management restores visibility and reduces business risk.


.svg)
.svg)
.svg)
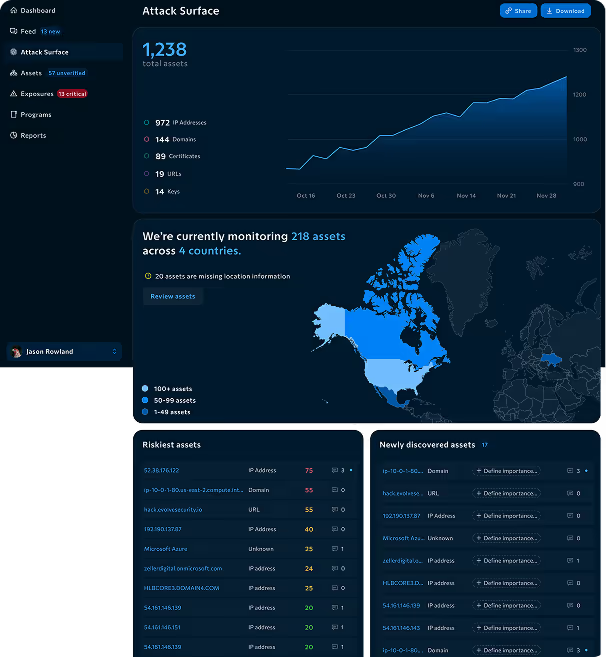


.png)


.png)