The CTEM Chronicles: The Industry’s First CTEM Maturity Model
“Are we there yet?”
You might be just starting out with CTEM or through your first cycles and find yourself wondering.
“Are we actually making progress with CTEM... or just renaming our old vulnerability management process?”
You’ve rolled out new tooling. You’re patching faster. Maybe you’ve even run a few attack simulations or exposure assessments. But when your CISO or board asks, “Where are we on the CTEM journey?” it’s hard to give a straight answer.
There’s no standard. No benchmarks. No roadmap.
Without a clear picture of what CTEM maturity looks like, you can’t lead your team or your business, toward it.
That’s where this episode comes in.
Evolve Security has developed a practical maturity model for CTEM that reflects real-world adoption which will help you:
- Understand the key pillars of CTEM (Scope, Discovery, Prioritization, Validation, Mobilization),
- Identify what “good” looks like at different stages,
- And shift the conversation from patch rates to strategic outcomes.
We’re not here to hand out report cards. This model isn’t linear or rigid because neither is your business. However, it will give you language, clarity, and a way to show progress.
1. Why Maturity Models Matter
Most of the security programs we see in the wild are built on a patchwork of inherited tools, inherited processes, and inherited problems.
When CTEM enters the picture, your natural instinct may be to apply it on top of what you already have. Rebrand a few workflows, add another dashboard, perhaps run some exposure assessments and call it a day.
However, without a maturity model a shared way of thinking about progress you’re flying blind.
You Can’t Improve What You Can’t Describe
CTEM isn’t just a set of actions. It’s a shift in mindset. A move from being reactive and compliance-driven to being proactive, focused, and strategic.
A maturity model gives you a framework to:
- Understand where you are now.
- Define what “better” actually looks like.
- Get buy-in from stakeholders who need to see progress in plain language.
Escape the “Activity Trap”
Ever feel like your team is doing more, but not actually improving? That’s the activity trap and CTEM is especially vulnerable to it.
Progress in CTEM isn’t about doing more it’s about doing the right things with the right focus. A maturity model gives you a lens to prioritize effort, not just count effort.
You Need a Better Way to Communicate Progress
Nobody outside your team cares how many CVEs you closed last month. What the business does care about is risk. Exposure. Resilience.
It turns vague progress into a story with chapters, and you get to show them which chapter you’re writing now.
2. Traditional Vulnerability Management vs CTEM
If you're still managing vulnerabilities the same way you did five years ago, you're not alone but you're also fighting against a growing tide.
Traditional vulnerability management focused on identifying and patching known issues, driven by CVE scores and scan cycles.
Traditional VM: Busywork Disguised as Progress
In a traditional VM model, the rhythm is predictable:
- Run scans.
- Get long lists of CVEs.
- Prioritize by CVSS score.
- Create tickets.
- Chase teams to close them.
- Report patch rates.
It looks like activity, but what it rarely gives you is confidence.
CTEM: A Strategic, Risk-Centric Shift
Instead of asking “what vulnerabilities exist?”, CTEM asks:
- What’s exposed?
- What’s exploitable?
- What’s impactful to the business?
- What’s actually worth fixing?
3. The CTEM Maturity Model Unpacked
Let’s get one thing straight: CTEM maturity isn’t a straight line.
Some parts of your program might be advanced, while others are still stuck in old habits. And that’s okay.
This maturity model isn’t about scoring you. It’s about helping you see where you are, where you’re strong, and what to improve next.
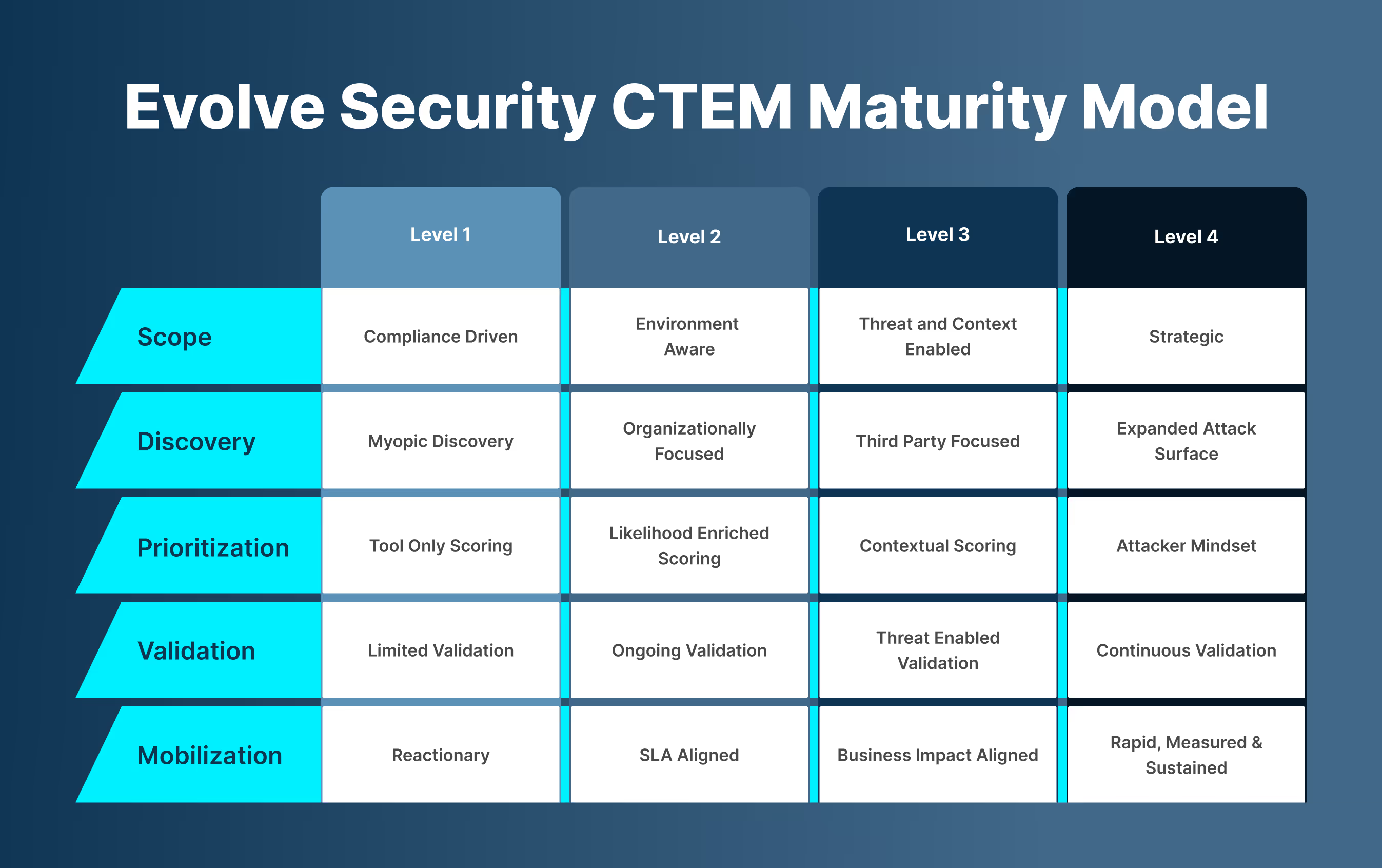
This maturity model helps you tell a better story about your program: not just what you’re doing, but how you’re evolving.
4. Key Domains to Measure Maturity
Let’s break each phase down further so you can understand how maturity plays out in the real world:
SCOPE
- L1: Compliance Driven - Focused on meeting regulatory requirements with limited visibility beyond alignment to contractual or regulatory requirements, “checking the box”.
- L2: Environment Aware - Starting to understand where critical assets and applications regardless of where they’re based.
- L3: Threat and Context Enabled - Scope includes critical assets and known attacker interests and considers business initiatives ( such as upcoming launches, acquisitions, etc.)
- L4: Strategic - Continuously and dynamically updated based on business operations and threat evolution.
DISCOVERY
- L1: Myopic Discovery – Basic scans, limited visibility and long durations between scans.(Quarterly to annual)
- L2: Organizationally Focused – Covers known assets across traditional patchable IT estate.
- L3: Third Party Focused – Includes vendors, SaaS, and partners.
- L4: Expanded Attack Surface – Comprehensive, including cloud-native and external assets.
PRIORITIZATION
- L1: Tool Only Scoring – Based on CVSS or tool output alone.
- L2: Likelihood Enriched Scoring – Adds exploitability context(EPSS) and/or KEV
- L3: Contextual Scoring – Considers business value, risk impact, and attacker attractiveness.
- L4: Attacker Mindset – Prioritizes based on real-world attack paths and internal and external threat data.
VALIDATION
- L1: Limited Validation – No confirmation of actual exploitability.
- L2: Ongoing Validation – Periodic tests, more hands-on.
- L3: Threat Enabled Validation – Simulated attacks confirm real exposures.
- L4: Continuous Validation – Automated, ongoing, and part of day-to-day operations.
MOBILIZATION
- L1: Reactionary – Action only happens under pressure.
- L2: SLA Aligned – Action is tied to timelines, not risk.
- L3: Business Impact Aligned – Acting based on business impact.
- L4: Rapid, Measured & Sustained – Fast, integrated, efficient, and measured efforts across teams.
5. How to Use the Model in the Real World
Use It as a Baseline, Not a Scorecard
Map where you are honestly. No one starts at Level 4. Use this to get your bearings and highlight where to focus next. Spot Where to Focus Next. Are you great at discovery but weak on mobilization? That’s your bottleneck. The model helps you focus your efforts and get unstuck.
Make It a Living Framework
Use this model in quarterly reviews, strategy planning, and stakeholder briefings. It’s not static, it should evolve with your program.
6. Closing & What’s Next
You now have a clear, practical model to define your CTEM journey and more importantly, to communicate it.
This isn’t about ticking boxes. It’s about transforming how you manage exposure, reduce risk, and lead security forward.
Join the conversation
Watch the expert-led webinar "A Case for CTEM" hosted by Evolve Security, featuring insights from industry leaders Paul Petefish, Jason Rowland, and Victor Marchetto. Discover best practices, strategies, and solutions for Continuous Threat Exposure Management (CTEM) to strengthen your cybersecurity posture.
Episode 8 Preview
Next time, we’ll break introduce a fictional case study so you can see the CTEM and journey in action.













