A NEW ERA OF OFFENSIVE SECURITY
Our innovative crew is flipping the switch on traditional testing by introducing a new era of offensive security by combining breakthrough technology with elite human expertise. This leadership is accelerating innovation and raising the bar for the entire industry.

Client Outcomes

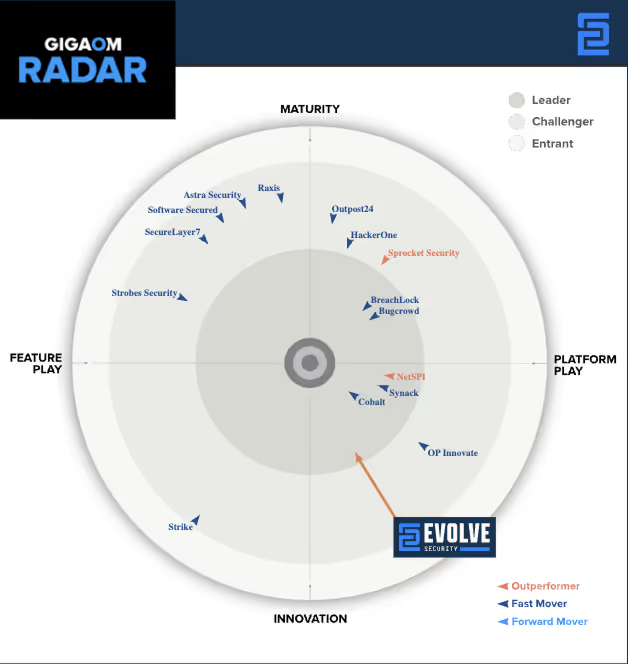
Evolve Security recognized as:
Leader and outperformer
in GigaOm Radar for PTaaS.
Recognized as 1 of 16 PTaaS leading vendors in the penetration testing market.
Only 1 of 2 PTaaS Vendors selected in 2025 GigaOm Radar as "Leader & Outperformer" in 2025.
Creating Raving Fans
The ultimate measuring stick is our client's success and increasing business resiliency.
4.8/5
G2 Customer Reviews






4.5/5





Gartner Peer Insights
80
Our client’s loyalty tracked in real time
NPS Score

Global InfoSec Award Winners:
Attack Surface Management and Continuous Penetration Testing
CYBER PIONEERS ASSEMBLED
For our journey, to change the offensive security industry, hear your peers share why they have joined our mission.
Client Case Study
Securing homegrown apps & LLMs with continuous penetration testing and threat modeling

Client Profile
A private equity firm that specializes in providing flexible capital solutions to growth-oriented companies. The firm typically invests in sectors such as:
- Software
- Digital infrastructure
- Healthcare IT
- Financial technology & services
- Business services

The Challenge
The client initially approached Evolve Security seeking guidance on securing core applications and LLMs that allow their analysts to make informed investing decisions. The lack of mature standards and governance frameworks left them:
- Experimenting with ad-hoc defenses
- Lacking consistent protections As potential threats against these assets escalated, the client began seeking a more proactive solution—one that could deliver:
- An initial threat model
- Continuous offensive pressure against their infrastructure

Solutions & Outcomes
Transitioned the client from to a true continuous penetration testing model, powered by its proprietary Darwin Attack™ platform.
- Reduced time to vulnerability validation by 68% (compared to quarterly pentests).
- Achieved 96-hour average remediation feedback loops—compared to 30+ days in legacy testing cycles.
- Identified and validated critical vulnerabilities within 24 hours of exposure going live, preventing real-world risk.






















