Tools of the Trade: Navigating Networks with Nmap

Introduction
In this blog I will be focusing on Nmap (Network Mapper), a powerful and versatile open-source utility that has established itself as an indispensable tool in the realm of penetration testing.
Nmap, as a network scanning and reconnaissance tool, would fall under the "Reconnaissance" tactic in the MITRE ATT&CK framework. Specifically, the technique it aligns with is "T1046 - Network Service Scanning". This technique refers to scanning networks to identify running services and open ports, which is one of the primary functions of Nmap.
However, Nmap's versatility allows it to potentially fall into more than one category within the framework. For instance, Nmap's scripting capabilities enable it to perform various tasks, such as vulnerability scanning or brute-forcing, which may correspond to different techniques in the ATT&CK framework. This multifaceted nature makes Nmap a valuable tool for pentesters, who can leverage its capabilities for a wide range of purposes.
Why Nmap Is Essential for Pentesters
In the world of pentesting, Nmap’s versatility and compatibility across various platforms allow pentesters to seamlessly carry out their tasks, while its comprehensive scanning capabilities, including port scanning, version detection, and OS fingerprinting, ensure that they can accurately assess the security of their targets. Additionally, Nmap's active community and continuous updates ensure that the tool remains current with the latest security threats and vulnerabilities. This ongoing development significantly enhances the effectiveness and reliability of Nmap for penetration testing professionals.
Common Nmap Scanning Techniques
Pentesters employ a variety of Nmap scanning techniques to evaluate the security of networks and systems effectively. Remember, it's crucial to ensure that you're only scanning networks you have permission to access. The use of Nmap can vary depending on the scope of the penetration testing. In some cases, you may need to perform a wide network scan, while in others, a more targeted or stealthy approach may be required.
For the sake of this demonstration, I'll be using "hack.evolvesecurity.io" as my target. Please note that this target has been intentionally designed for educational purposes, and all critical information and systems involved are purely fictional.
Among the most common techniques, the ping scan (ICMP sweep) enables pentesters to quickly identify live hosts by sending ICMP echo requests and awaiting responses. By using the "-sn" flag, pentesters can perform a ping scan with ease.
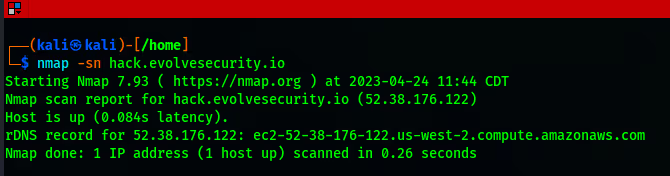
Additionally, port scans (TCP, UDP) provide invaluable insight into open ports and services on target systems, utilizing flags such as "-p" for specifying ports, and "-sT" or "-sU" for TCP and UDP scans, respectively.
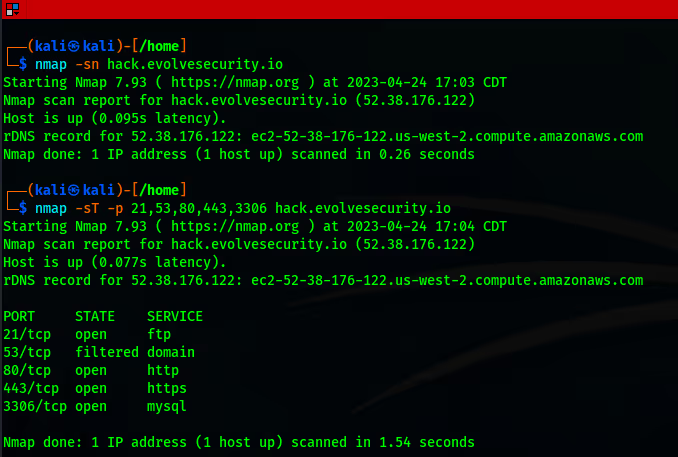
To delve even further, version detection scans help identify the exact software and version running on open ports, which can be initiated by employing the "-sV" flag. As well as OS fingerprinting, which offers the ability to make an educated guess on the operating system of target devices, using the "-O" flag.
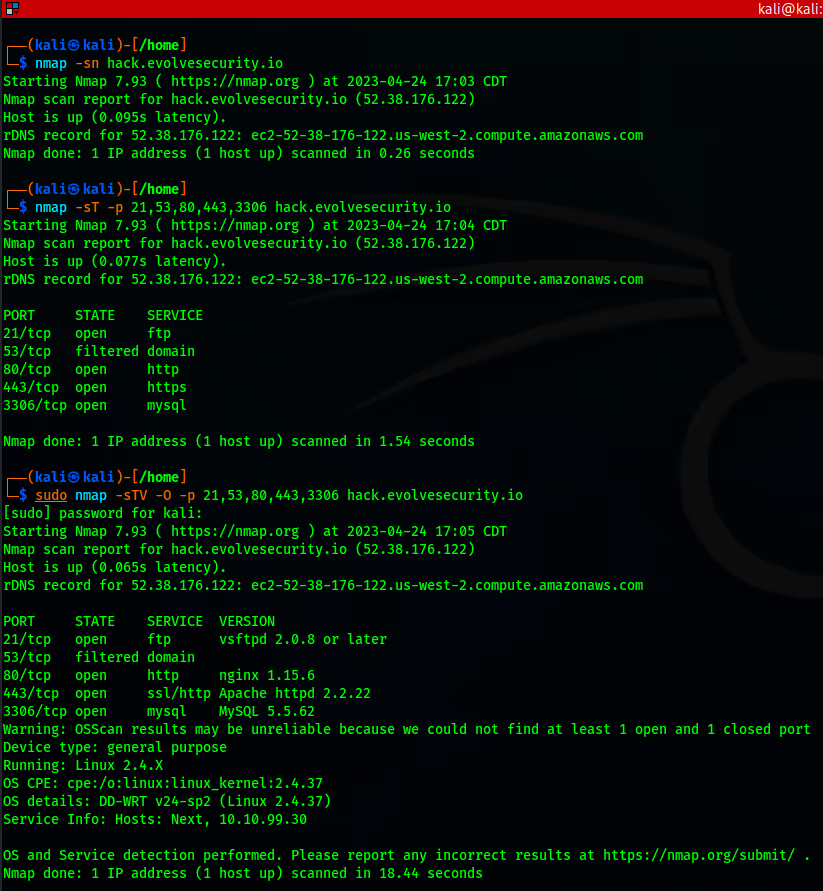
By leveraging Nmap’s diverse scanning techniques, pentesters can effectively detect potential vulnerabilities, misconfigurations, and weak points within network infrastructure. As pentesters identify and report these findings, they provide invaluable insights to organizations, enabling them to address security gaps and implement effective remediation strategies. This collaborative approach strengthens security posture and helps to protect valuable assets from potential cyber threats.
Real-World Nmap Pentesting Scenarios
Vulnerability Assessment
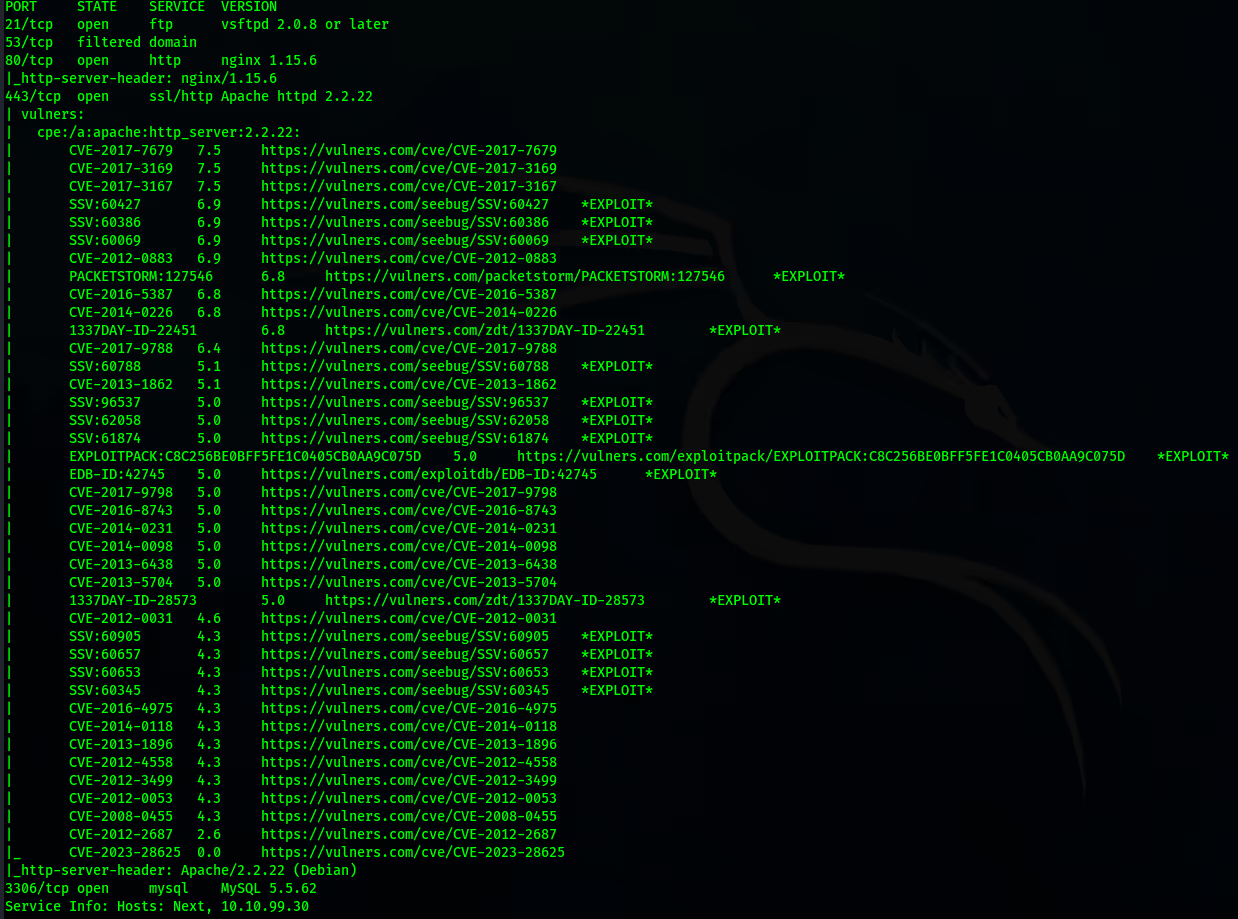
Nmap's scripting engine allows pentesters to check for specific vulnerabilities using Nmap Scripting Engine (NSE) scripts.
For example, a pentester might use the "vulners" script to identify potential vulnerabilities in detected services: nmap -sV --script vulners “target”
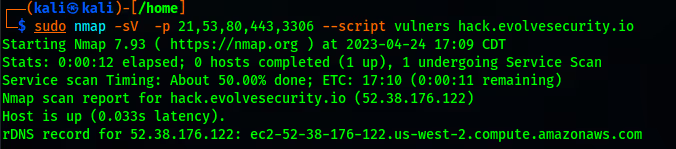
This command scans the target for service versions and checks them against the Vulners database for known vulnerabilities.
Exploit Validation
After exploiting a vulnerability, a pentester can use Nmap to confirm that they have successfully gained access to the target system.
For example, if they have exploited a vulnerability in a web server and opened a reverse shell on port 4444, they can use Nmap to check if the port is indeed open: nmap -p 4444 “target”
This command scans the specified port (4444) on the target IP to confirm that it is open and accessible. If the port is indeed open, the output will show "4444/tcp open". This indicates that the reverse shell is running and listening on the target machine, and the exploit has been successful.
Legal and Ethical Considerations
Before performing any testing, it is crucial for pentesters to obtain permission from the network owner or administrator. A preliminary meeting should be arranged to discuss the scope, objectives, and boundaries of the engagement. This step ensures that both parties have a clear understanding of the testing process and expectations, as well as minimizing the risk of unintended consequences or legal issues.
Establishing a well-defined scope allows penetration testers to focus their efforts on areas of interest. By following these legal and ethical considerations, pentesters perform their testing in a responsible and professional manner, ensuring the security of the target network and preventing any harm or damage.
Conclusion
Nmap is an indispensable tool for pentesters when evaluating the security of networks and systems. Its versatility and compatibility across various platforms makes it a valuable asset in any pentester's toolkit. Nmap's comprehensive scanning capabilities allow pentesters to gain a thorough understanding of their targets and detect potential vulnerabilities effectively. Nmap’s ongoing development ensures that the tool remains current with the latest security threats and vulnerabilities, enhancing its effectiveness and reliability for penetration testing professionals.
It is important to remember the legal and ethical considerations when performing any testing, emphasizing the need for permission, responsible disclosure, and adherence to ethical hacking guidelines. By following these ethical considerations, pentesters perform their testing in a professional manner, ensuring the security of the target network while preventing any harm or damage.

.avif)











