Tools of the Trade: Vulnerability Scanning with Nessus

Introduction
Throughout a penetration test, cybersecurity professionals rely on a variety of cutting-edge tools that help them uncover and address vulnerabilities. Among these tools, Nessus stands as a popular choice for many. Nessus is a vulnerability scanner developed by Tenable that scans for known security flaws, misconfigurations, and weaknesses, and then provides detailed reports on the findings, along with remediation recommendations.
In this blog, I will delve into how pentesters utilize Nessus to efficiently identify weaknesses within networks, applications, and systems.
The Pentester's Approach to Nessus
Selecting Nessus as the vulnerability scanner of choice
Nessus stands out when conducting comprehensive security assessments due to its user-friendly interface and extensive library of plugins. Its continuously updated vulnerability database further adds to its invaluable utility. By leveraging the tool's strengths, pentesters can efficiently identify an organization's security weaknesses and address potential threats. With its ability to scan a wide range of systems and network devices, Nessus equips pentesters with invaluable insights that can be used to develop tailored solutions to fortify the security posture of their clients.
However, as with any tool, Nessus has limitations that must be considered in the context of a holistic security assessment, and it is crucial for pentesters to complement the scanner's findings with their own expertise and manual testing techniques.
Aligning Nessus with pentesting methodologies
To ensure comprehensive and accurate testing, pentesters align Nessus with various methodologies such as black-box, white-box, and gray-box testing, ensuring a customized and targeted assessment of potential security risks. Each approach offers distinct advantages. Black-box testing provides an external perspective by simulating a real attacker without prior knowledge of the target system. White-box testing delves into the system's source code and architecture, allowing for thorough analysis and identification of vulnerabilities. Lastly, Gray-box testing combines aspects of both black-box and white-box testing by granting the tester partial knowledge of the system's inner workings.
Integrating Nessus into the Penetration Testing Process
Utilizing Nessus in the reconnaissance phase
The reconnaissance phase is a critical stage in the penetration testing process, as it lays the groundwork for identifying potential targets and planning subsequent attack strategies.
Nessus not only efficiently scans IP ranges to identify live hosts and open ports but also generates comprehensive reports on network topology. The process of identifying live hosts narrows down potential targets, and the discovery of open ports reveals possible entry points for attackers. Simultaneously, by scanning entire networks, Nessus provides an in-depth understanding of the target environment. This detailed information includes the network's various components such as devices, hosts, and services, thus providing crucial information to pentesters during the reconnaissance phase.
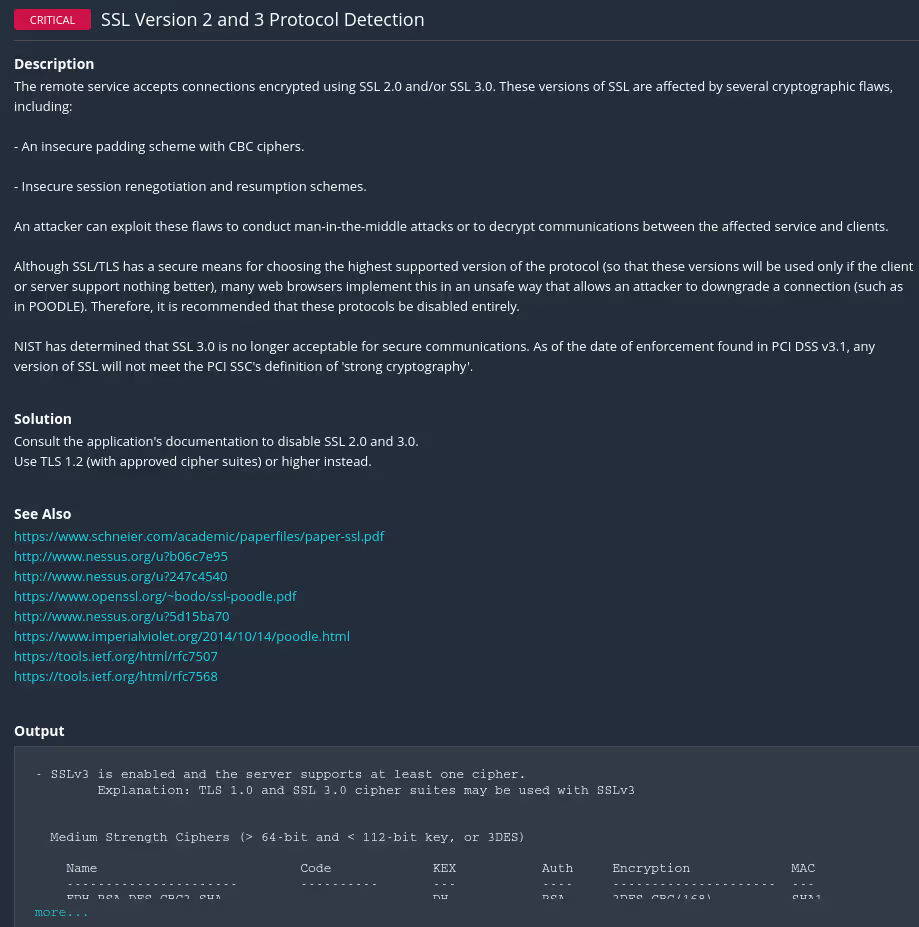
Information that was reported after a vulnerability was discovered using an Advanced Scan
Exploiting discovered vulnerabilities
Nessus maintains a vast database of known vulnerabilities and is regularly updated with newly discovered ones. By scanning target systems and networks, it can identify and report on vulnerabilities that may be present. Pentesters can then prioritize and exploit these vulnerabilities to gain unauthorized access or escalate privileges within the target environment.
Validating and verifying identified issues
After exploiting discovered vulnerabilities, it is essential for pentesters to validate and verify the identified issues. Nessus assists in this process by providing detailed information on each vulnerability, including its severity, potential impact, and remediation recommendations.
Enhancing Nessus Scans with Pentester Expertise
Tailoring scans for web applications, infrastructure, or IoT devices
A one-size-fits-all approach rarely works in cybersecurity. Different environments and systems have unique security requirements, and it is essential for pentesters to tailor their Nessus scans accordingly. By customizing scan policies, pentesters can focus on specific types of vulnerabilities, be it web applications, infrastructure, or IoT devices. This targeted approach not only saves time but also helps to identify potential weaknesses that might otherwise be overlooked.
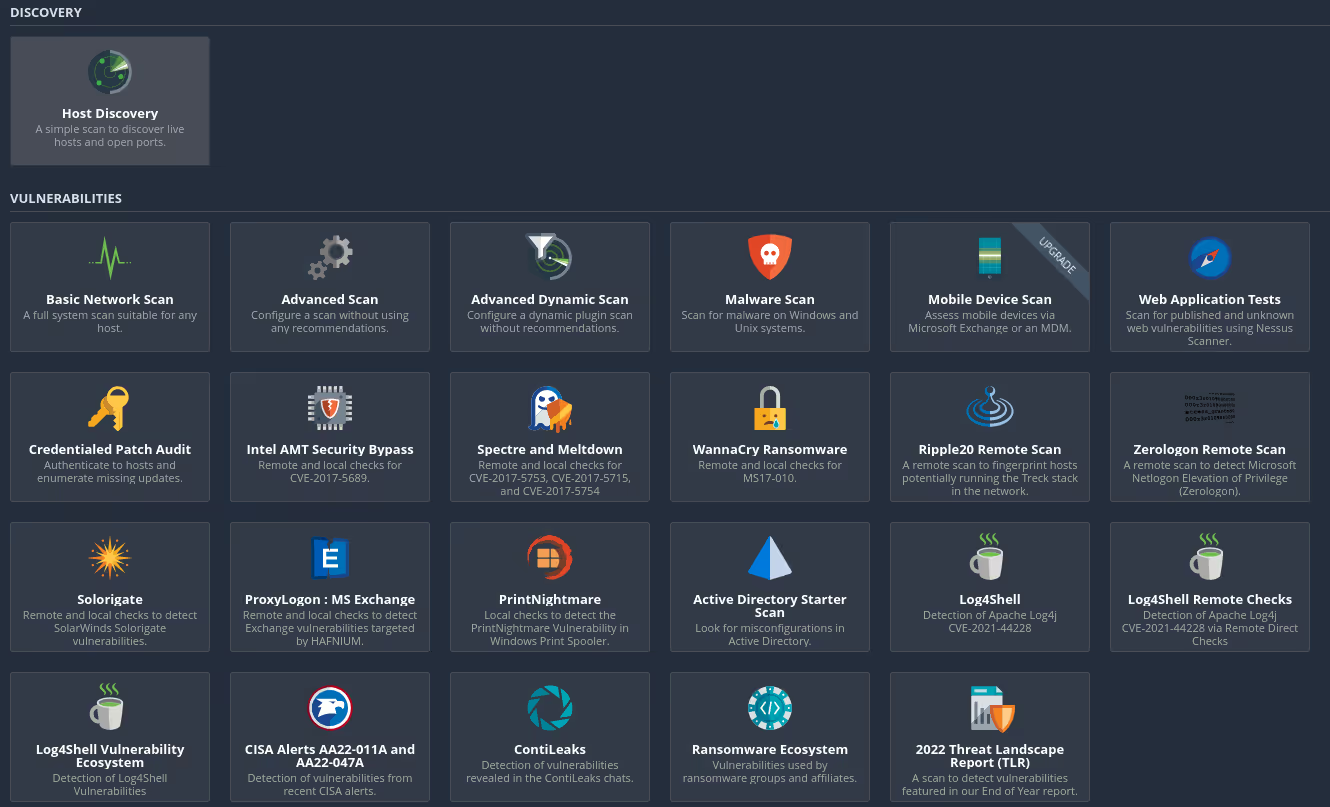
Discovery and Vulnerability Scan options
Creating custom policies for industry-specific requirements
Organizations operating in specific industries often face unique regulatory requirements and security challenges. Pentesters can enhance the effectiveness of Nessus scans by creating custom policies that cater to these industry-specific needs. For instance, healthcare organizations need to comply with HIPAA regulations, while financial institutions must adhere to PCI-DSS standards. By incorporating these standards into custom Nessus policies, pentesters can help their clients maintain compliance while also ensuring a high level of security.
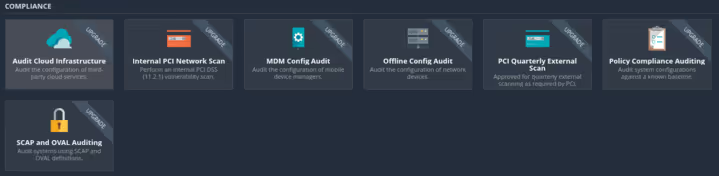
Compliance Scan options
Analyzing scan results for accuracy
One of the challenges of using Nessus is the risk of false positives. To combat this issue, pentesters analyze the results of scans, filtering out potential false positives by cross-referencing the findings with their knowledge of the target system and known vulnerabilities. This analysis ensures that the identified issues are genuine security risks that warrant further investigation.
Confirming vulnerabilities with manual tests
After eliminating false positives, pentesters go one step further by manually validating the remaining vulnerabilities. This process confirms that a specific vulnerability can be exploited, as well as assessing its potential impact on the target system. By combining the power of Nessus with the hands-on expertise of pentesters, organizations receive a comprehensive and accurate security assessment that helps them prioritize remediation efforts and safeguard their assets.
Conclusion
In conclusion, Nessus plays a vital role in a pentester's toolkit, providing comprehensive vulnerability scanning, assessment, and reporting capabilities. The key to unlocking Nessus' full potential lies in the commitment to continuous learning and adaptation, encouraging pentesters to stay one step ahead of adversaries and maintain the highest level of protection for their clients.

.avif)











