Tools of the Trade: Taming Burp Suite
Introduction
Burp Suite is one of the most popular tools released when discussing web application penetration testing. With an easily understandable user-friendly interface, Burp Suite streamlines the process of identifying and exploiting vulnerabilities within a web application.
From crawling web applications to intricate manual testing, features such as “Intruder” and “Repeater” are just a few of the powerful functionalities that allow for tailored testing. In this blog, we will be exploring Burp Suite Community Edition.
All attacks shown in this blog are performed against an intentionally vulnerable web application hosted by Evolve Security at (hack.evolvesecurity.io). Anyone is welcome to practice attacks against this web application which resets every day at 2am CST.
Core Features of Burp Suite
The Community edition of Burp Suite provides essential functionalities like the “Target”, “Proxy”, “Intruder”, and “Repeater” tabs.
When starting off any engagement, it is essential to make sure the scope is set to only interact with the intended web application. This can be done by editing the “Scope settings” within the “Target” tab of Burp Suite. This critical step ensures that only traffic from targets within the scope of the engagement can be viewed, passively crawled, and modified.
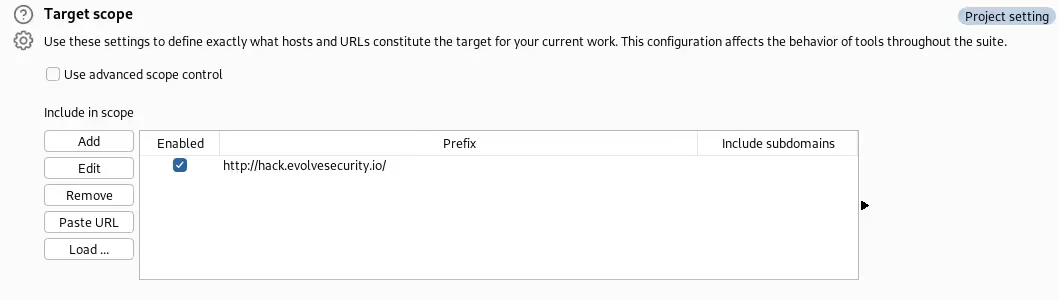
Target
The “Target” tab in Burp Suite automatically builds out a site map of the pages visited within the scope set by the user. The user can then go back through the site map for further in-depth analysis of the web application. The site map is expanded as the user continues to visit different pages around the application. The requests to each of these pages are stored in the site map, providing the user with more information as they go throughout their web application assessment.
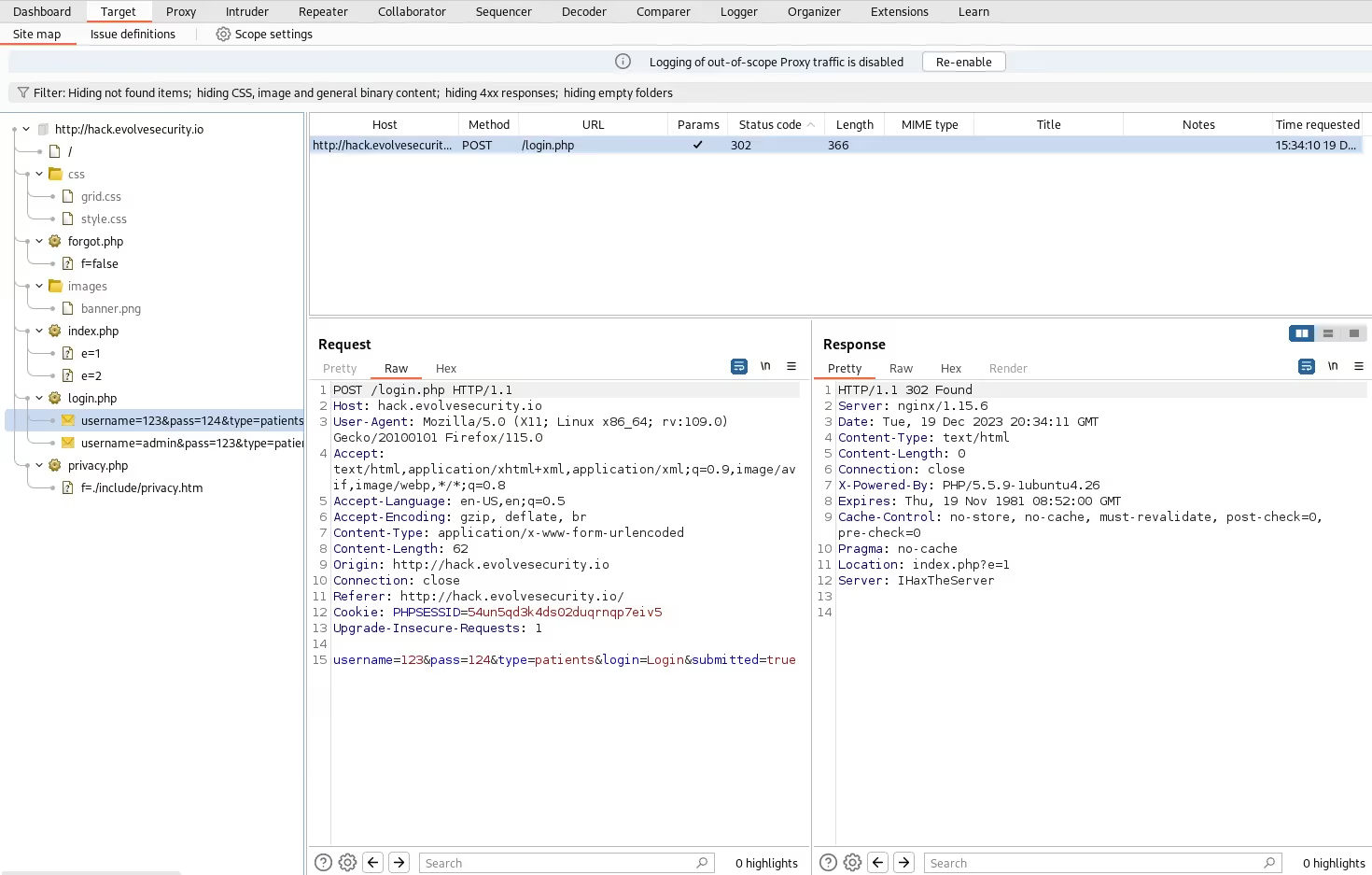
Proxy
When “Intercept” is turned on, the “Proxy” tab is populated with the current requests going through the browser. The user can set this up multiple ways, the most popular being the use of the Firefox addon Foxy Proxy. The user can inspect and edit these individual requests and then determine if they are forwarded to the browser or dropped. This functionality gives users the ability to see how their requests are being sent to the web application while simultaneously expanding their site map displayed within the “Target” tab.

Intruder
The “Intruder” tab is used for automating attacks against web applications. From Credential Stuffing to Password Spraying, “Intruder” is easily one of the most used functions within Burp Suite.
When using the “Intruder” tab, there are multiple ways to combine and send payloads to a target. First the user would send the request they’d like to test from the “Proxy” or “Target” tab to the “Intruder” tab by right clicking and selecting “Send to Intruder”. If the user is attempting a Password Spraying attack on a web application, they would be using the “Sniper” attack to specify the username field to attack. Keeping the password they want to use unchanged throughout the duration of the attack. The user would then add their desired usernames to the payload list. After adding the usernames, the user would start the attack and review the results for any abnormalities in status code or content length. This process can be aided by using prebuilt and custom filters.


Repeater
The “Repeater” tab in Burp Suite, akin to the “Proxy” tab, is a vital tool in web application testing. This tab allows users to send a request from the “Proxy” tab to the “Repeater”, where they can repeatedly modify and resend it to analyze the web application’s responses. This feature is particularly useful for testing different payloads and observing how the application reacts, especially in terms of HTTP response codes and other critical response details.
By altering various aspects of the request, such as parameters and headers, testers can probe for vulnerabilities like SQL injection and XSS. This type of testing is crucial for understanding how the application processes and validates data, a key factor in identifying vulnerabilities.
Additionally, this tab is instrumental in assessing authentication and authorization mechanisms by tweaking session tokens and cookies in requests. This manual approach of crafting requests offers precision that automated tools lack.
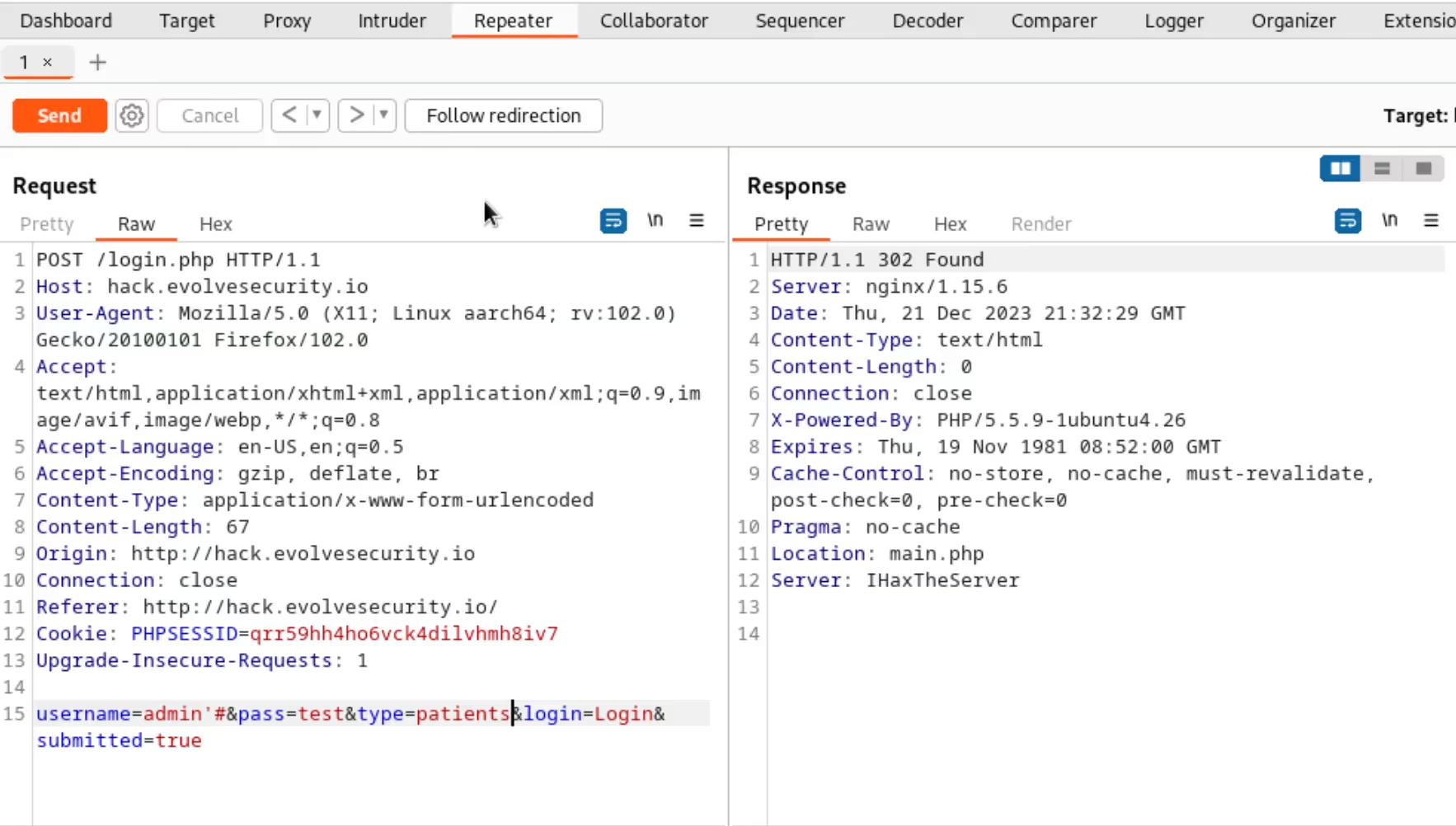
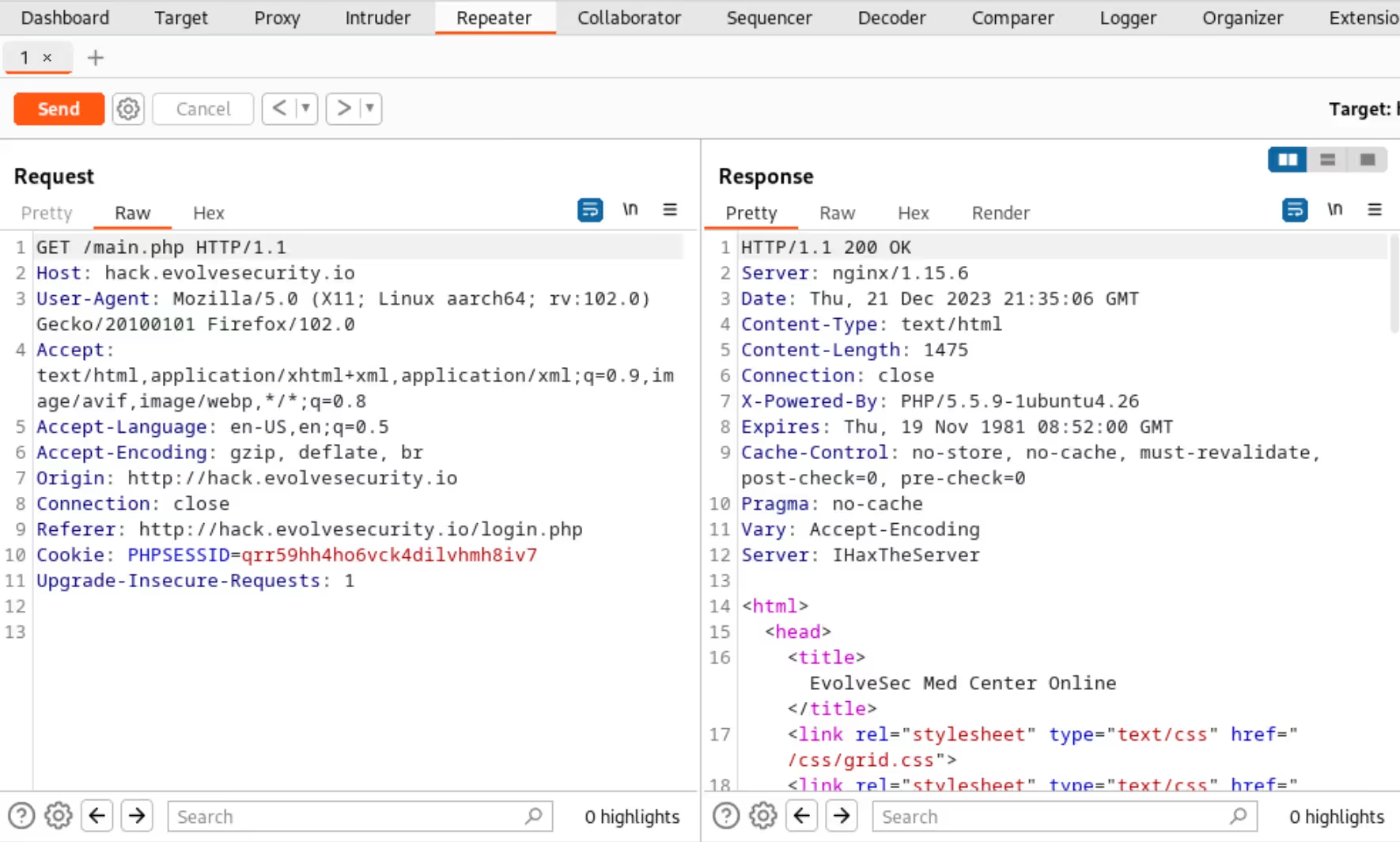
Conclusion
Burps Suite’s strength lies in its ability to act as an all-in-one platform, combining various tools for different aspects of web application testing. Burp Suite's “Proxy” feature allows testers to intercept and analyze traffic between the browser and the target application, providing deep insights. This interception capability is critical for understanding how applications handle data and for identifying vulnerabilities. The “Intruder” and “Repeater” functions are two more key features, allowing customized attacks on application parameters, and thorough testing of individual requests.
Burp Suite’s user-friendly interface, combined with advanced manual testing capabilities, makes it suitable for both novice and experienced penetration testers. Overall, Burp Suite stands out as a comprehensive and flexible tool, essential for any thorough and effective web application testing process.

.avif)











