The CTEM Chronicles: Why You Should be Paying Attention to CTEM
This may resonate with you…
Your vulnerability scanner just dumped another 700 findings into your backlog while your team is wearing more hats than seems reasonable. Leadership is asking if you’re “secure” (whatever that means) and your pen testers keep finding the same stuff every quarter.
You’re doing everything you’re supposed to do: scanning, patching, possibly even threat modelling and red teaming. But nothing feels strategic. You’re stuck in reactive mode, running in place.
If that sounds familiar, you’re not alone. This is why CTEM (Continuous Threat Exposure Management ) is getting lots of second looks.
CTEM is a way to break the cycle. Instead of reacting to every scan result or audit finding, it helps you focus on what actually matters: the exposures that real attackers could exploit right now, in your environment, based on your business priorities.
In this article we aim to provide a clear understanding of:
- What CTEM is.
- Why now is the time to start caring about it.
- Whether it’s something you can realistically adopt.
Let’s begin.
What is CTEM?
Behind yet another acronym is a powerful concept. Continuous Threat Exposure Management (CTEM) is about seeing your environment the way an attacker would, and then doing something meaningful about it.
CTEM is not a product.
It’s a methodology that helps you constantly identify and reduce the ways your organization could be compromised.
Think of it like this: traditional security programs often look at risk in isolated buckets (vulnerability management, pen testing, red teaming, config audits). CTEM connects all of these and allocates them against business priorities. It gives you a framework to continuously:
- Scope what assets and environments to assess
- Discover exposures across them (not just vulnerabilities)
- Prioritize what matters most
- Validate that the threats are real and exploitable
- Mobilize your teams to fix what counts
So instead of chasing endless CVEs or reacting to pen test reports months later, CTEM keeps your focus sharp. It’s about exposure management that’s ongoing, contextual, and operational.
If that still sounds abstract, here’s a quick contrast to bring it to life:
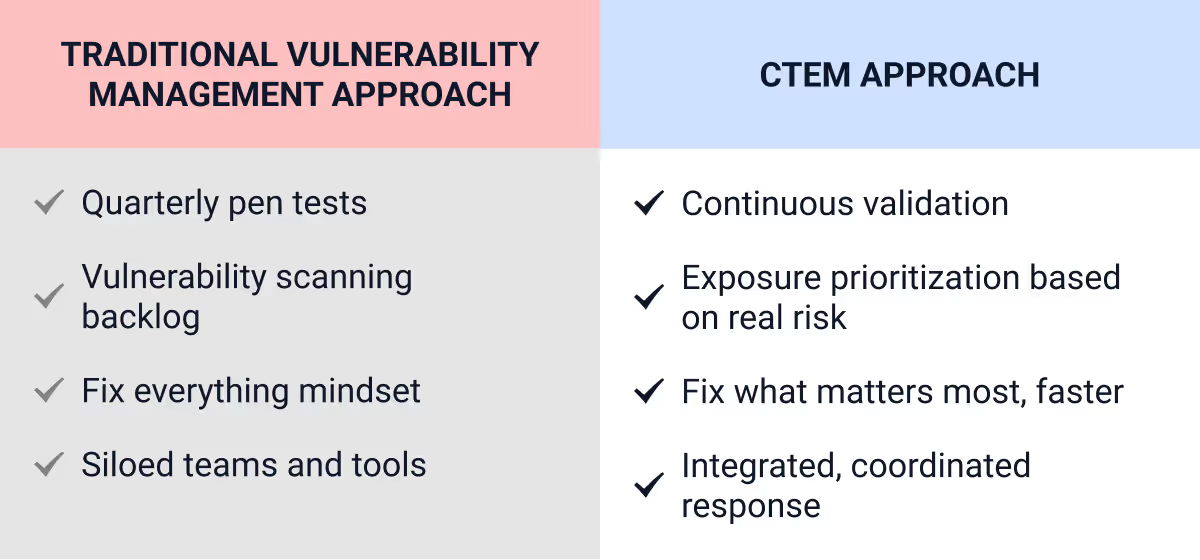
Bottom line: CTEM is less about adding more tools, and more about making better decisions with the ones you already have.
Why Now?
A few years ago, you had a clear perimeter, a handful of critical assets, and a decent grasp on what your environment looked like. Today? You’ve got cloud infrastructure, third-party integrations, remote endpoints, and shadow IT, Generative AI cropping up everywhere… and that’s just Monday.
Your attack surface is change as it grows. The attackers aren’t sitting still either, they’re moving faster, automating reconnaissance, and exploiting misconfigurations and overlooked exposures quicker than in years past.
Here’s the uncomfortable truth: most breaches don’t happen because of unknown zero-days. They happen because of stuff you already know about but haven’t fixed, or didn’t know was exposed in the first place. It’s an unfortunate reality we see playing out in the news every day.
CTEM offers a way to alter the paradigm. It’s built for the world you’re operating in now, where visibility is fragmented, resources are stretched, and priorities are unclear.
It gives you a way to:
- Stay continuously aware of your exposure
- Make smart, contextual decisions about what to fix
- Prove to your stakeholders that you're reducing risk, not just chasing noise.
In other words, CTEM helps you go from reactive guesswork to proactive control.
How is CTEM Different From What You’re Already Doing?
At first glance, CTEM might sound like a remix of things you’re already doing, vulnerability scanning, threat modelling, red teaming. The key difference is this: CTEM isn’t about doing more, it’s about doing it differently and doing so with coordination with the business.
Here’s what usually happens without CTEM:
- Your vulnerability scanner spits out a mountain of CVEs.
- Your pen testers find something critical every quarter (but too late).
- Your red team gets blocked by controls that don’t exist in prod.
- Your remediation teams get overloaded with generic tasks that don’t reduce real risk.
It’s fragmented. It’s reactive. And most of the time, the things that actually matter get lost in the noise.
CTEM changes that by giving you structure, sequencing, and context.
Instead of treating each security activity like a separate event, CTEM weaves them into a cycle:
- You start by scoping what’s in bounds (your crown jewels, cloud infrastructure, specific environments).
- You discover exposures, not just vulnerabilities, but weak configs, attack paths, user behaviors.
- You prioritize based on real-world risk defined by what currently is exploitable, exposed, and important.
- You validate what attackers can actually do through testing and emulation.
- You mobilize the fix, align the right teams, at the right time, using clear evidence.
This means your efforts are no longer scattershot. You’re not patching just to patch, or testing just to tick boxes. You're taking targeted action to close off the paths attackers are most likely to take.
CTEM turns your security program from a bunch of disconnected tasks into a continuous, strategic operation. That’s the difference.
The Real Benefit: Prioritization with Purpose
If we’re being honest with ourselves, we’re never going to fix everything. Not because your team isn’t capable, but because your resources are limited, your systems are complex, and the threat landscape never stops moving.
It’s not about perfection, it’s about precision.
The real power of CTEM is in how it helps you to isolate what events will actually your organization at risk right now. Instead of reacting to every new CVE, we should ask ourselves:
- Is it exploitable in your environment?
- Is it accessible to an attacker?
- Does it impact a critical asset?
- Can it be chained with another exposure to create a real-world attack path?
When you start answering those questions, it becomes much easier to decide where to spend your limited time and effort.
This isn’t just good for your IT and Security team, it’s beneficial across the board.
- Executives see clearer risk reduction metrics.
- Ops teams get fewer, more focused tasks.
- Security teams shift from firefighting to forward planning.
Where To Go From Here?
We don’t have to start from scratch, just take a fresh perspective on a familiar problem. CTEM is about changing how your organization approaches managing exposure, so it can do so continuously and with intention.
Now that you’ve got a solid handle on what CTEM is and why it matters, the next step is breaking it down into actionable chunks.
That’s exactly what the CTEM Chronicles will cover. In this series, you’ll get a practical walkthrough of each CTEM phase:
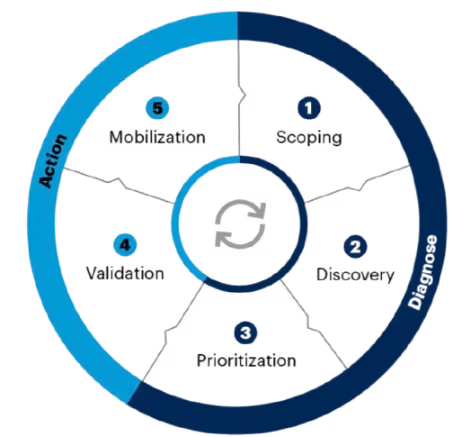
- Scoping – how to define what to include in your exposure assessments and why that matters.
- Discovery – how to go beyond traditional vuln scanning to uncover real attacker entry points.
- Prioritization – how to zero in on what’s high impact in your environment.
- Validation – how to confirm whether those risks are exploitable, and by whom.
- Mobilization – how to get the right people to fix the right things, at the right time.
Each blog will show you what good looks like at that stage as well as how to avoid the common traps that make most security efforts stall.
CTEM is not a product. It’s a framework that can bring bring clarity, control, and impact to your security program.













