Pentester Perspective: Knowing the Difference Between Pentesting and Vulnerability Scanning
Vulnerability Scanning vs. Penetration Testing Goals
Vulnerability Scanning and Penetration Testing are two important, and often conflated, components of a comprehensive security program. Let's be clear: Vulnerability Scanning and Penetration Testing are not the same thing. While both are offensive security practices, they each serve distinct purposes and require different methodologies. Unfortunately, the rise of "automated penetration testing" services has further muddied the waters, blurring the lines between these two distinct approaches.
To understand the differences, it’s important to draw boundaries around the fundamental goal of each service. Scanning is a great solution for automated vulnerability discovery. Scanners help to quickly illuminate configuration issues, identify outdated libraries and services, and discover vulnerabilities across expansive surfaces. Proactive scanning is foundational for keeping assets up-to-date and weeding out common, dare I say, “low hanging fruit”, issues.
Vulnerability Scanning Outcome Goal:
Broad-sweeping vulnerability enumeration and discovery for proactive vulnerability management.
When it comes to Penetration Testing, there is a different, yet very explicit purpose; To simulate attacks on your organization conducted by a capable and motivated adversary. Attack chains can of course contain many automated tools and systems, but the ability to adapt to new scenarios, understand contextual relationships, identify chained attack paths, and exploit them requires human ingenuity and creativity.
Penetration Testing Outcome Goal:
Simulate realistic attacks to identify and demonstrate the impact of contextualized vulnerabilities across assets and systems.
Untangling The Two – Vulnerability Scanning
Vulnerability Scanning is a high-volume, request-driven process that generates a significant amount of data. Because the goal is not to mimic the behavior of attackers, scanning itself is noisy, usually to the tune of many hundreds of thousands of requests in a short duration. The output data from scans is usually significant, which, unfortunately can lead to vulnerability scan reports being passed off as a penetration test.
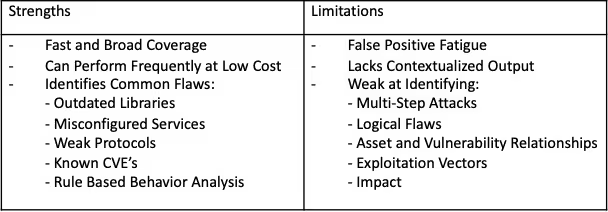
Vulnerability scanners work by sending requests to a pre-defined scope (e.g., A URL, Web Application, List of IPs or CIDRs), and analyze the response for things like: Server Version, Library Versions, Enabled Protocols, Discoverable Files, Default Configurations, and similar. The responses are checked against a large database, and if the identified version or configuration has an associated CVE or other known vulnerability, the scanner will flag it.
For example, scanners will flag the following based on basic the rule-check process:
- TLSv1.0, TLSv1.1
- Vulnerable JavaScript Libraries
- SSL Certificates and Cipher Suite Issues
Scan findings differ based on authenticated vs. unauthenticated configuration, as well as the focus of scope (e.g. Internal or External Network). In general, scan-produced vulnerabilities follow the schema of: Specific Product Version tied to Specific CVE.
Scanners also flag issues based by evaluating how a system responds to malformed or malicious input. Dynamic behavior analysis is particularly well-suited for identifying default or insecure configurations, along with injection-based vulnerabilities.
For example, by analyzing the response behavior, a vulnerability scanner may flag things like:
- SQL Injection
- Cross-Site Scripting
- LDAP Injection
Untangling The Two – Penetration Testing
Penetration Testing is focused on targeting specific elements of an environment (e.g. Cloud Infrastructure, Web Application, Internal Network), with the explicit purpose of identifying vulnerabilities, contextualizing issues, and demonstrating impact. In other words, pen-tests aim to answer the question of “So what?”.
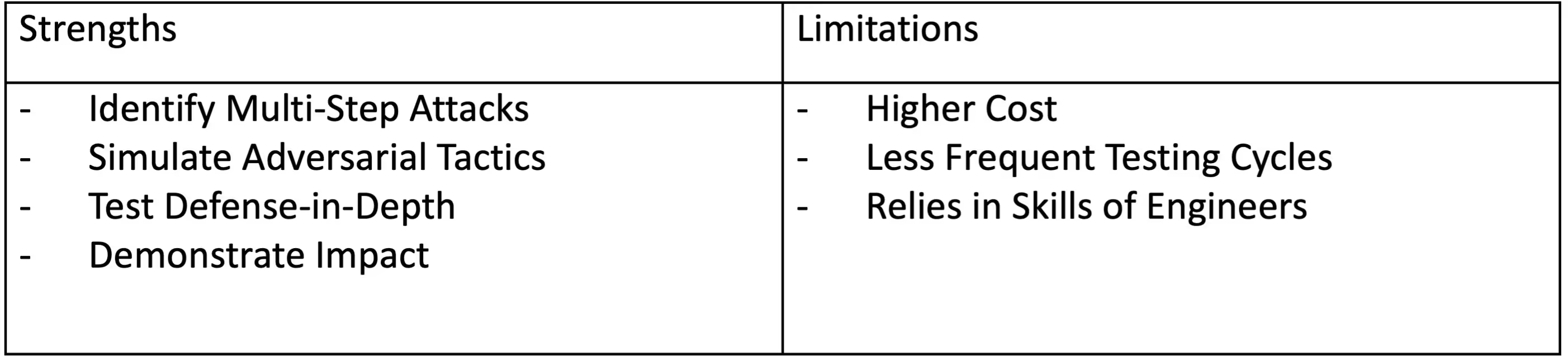
Penetration Testing begins with Vulnerability Scans. Scanning compromises ~10% of the total engagement and provides the engineer with a lay of the land to begin constructing more targeted testing. In this context, vulnerability scans help to emulate long-tail enumeration efforts within a drastically condensed timeframe.
The remaining ~90% of the penetration test cycles through an iterative workflow of manual enumeration and discovery, vulnerability chaining, research, and exploit attempts. During this time, the engineer not only assesses the vulnerability itself, but evaluates its relationship to the environment at large. The discoveries from penetration testing provide deeper insight into how real attack paths could emerge and demonstrate impact to drive actionable improvements.
One of the key differentiators between a Penetration Test and Vulnerability Scan is the ability for the penetration tester to build multi-step attack chains specific to the environment. For example:
A web application may have a low-severity vulnerability which allows for the Username Enumeration, and a medium-severity Client-side Input Validation vulnerability that allows registered users to bypass restrictions to update their email. On their own, neither poses significant risk, however, chained together, an attacker may be able to identify administrator accounts and the leverage the input validation issues to overwrite admin emails and overtake their accounts. It is not uncommon to see highly impactful attack chains begin with seemingly innocuous vulnerabilities.
Similarly, an attacker who gains access to an internal network through a phishing attack may notice that the printer is configured with default credentials. Not ideal, but seemingly not a big problem either. That is until the attacker uses the printer issue to perform a Pass-back-Attack, redirecting SMB or LDAP credentials back to the attacker-controlled machine. Often these captured credentials will have elevated privileges and can be the stepping-stone towards Domain-Admin compromise.
Through vulnerability chaining and multi-step attack chains, Penetration Tests illuminate how well (or not) Defense-in-Depth controls work. This is an invaluable outcome that cannot be achieved through vulnerability scanning alone.
Key Indicators to Help Differentiate Between Vulnerability Scanning and Penetration Testing
- Testing Timeframe Length: There is no hard-and-fast rule for how long a Penetration Test should take. Ultimately, as with any service, you’re trading time for money. Red-team engagements can span several months, and the price-tag will reflect it. Conversely, a strict time-boxed engagement with a set number of hours could be composed of a single testing day. Attackers have unlimited hours at their disposal, and the challenge then is striking the right balance between time and depth of coverage. Penetration Tests generally average about ~2 weeks (if the test takes a few days, it’s probably just a scan).
- Reporting Narratives: Vulnerability Scans produce a high-volume of data in the form a vulnerability finding tied to a host:port. Penetration Tests include this information, but importantly, should demonstrate a journey that examines the relationship between vulnerabilities, contextualizes issues specifically to your environment, explores impact, and describes the process of a human attempting to build realistic attack against the environment.
- Depth of Findings: Looking at the depth of findings in a report is usually a giveaway on whether the project was a Vulnerability Scan or a Penetration Test. Vulnerability Scan Reports flag vulnerabilities on a specific asset. Penetration Tests explore how a vulnerability an Host X relates to a vulnerability on Host Y, provides explanations for how attacks were conducted, and demonstrates impact beyond vulnerability discovery.
Don't leave your organization's security to chance—ensure you understand the critical differences between vulnerability scanning and penetration testing. Get started now to invest in the right security measures and secure your assets against potential threats.













