How Is a Posture Assessment Performed on an Organization?
Managing cyber risk is a complicated endeavor. Threat actors are constantly changing their tactics as our IT infrastructure and 3rd party relationships evolve. The public state of the art, what defenders are capable of, is chasing and reacting to the private state of the art, what threat actors are capable of. Even the most well-funded and capable cyber security teams struggle to approach the public state of the art. It is prudent to view cybersecurity as a process, not a product that can be bought nor a state that can be reached. The cybersecurity posture assessment can be a critical tool for performing two important parts of any cybersecurity program and ultimately to improve the process.
- What should we be doing to address the threats?
- What are the gaps between what we are currently doing and what we should be doing?
A cybersecurity posture assessment is a comprehensive evaluation of an organization's security position. It involves identifying potential threats and vulnerabilities to the company's infrastructure and assessing the effectiveness of existing security controls. Every organization faces different threats, and many organizations are unaware of the vulnerabilities those threat actors might exploit.
The posture assessment enables organizations to identify weaknesses in their cybersecurity program as well as the security systems that support it and take corrective measures to address risks. We will discuss the steps involved in a cybersecurity posture assessment and the benefits it can bring to an organization.
Understanding a Cybersecurity Posture Assessment
A cybersecurity posture assessment is a comprehensive review of an organization's security posture. This assessment helps organizations identify potential threats and vulnerabilities to their infrastructure and evaluate their security controls' effectiveness. A cybersecurity posture assessment also provides a roadmap for organizations to prioritize and remediate identified risks. There are 6 steps in this process.
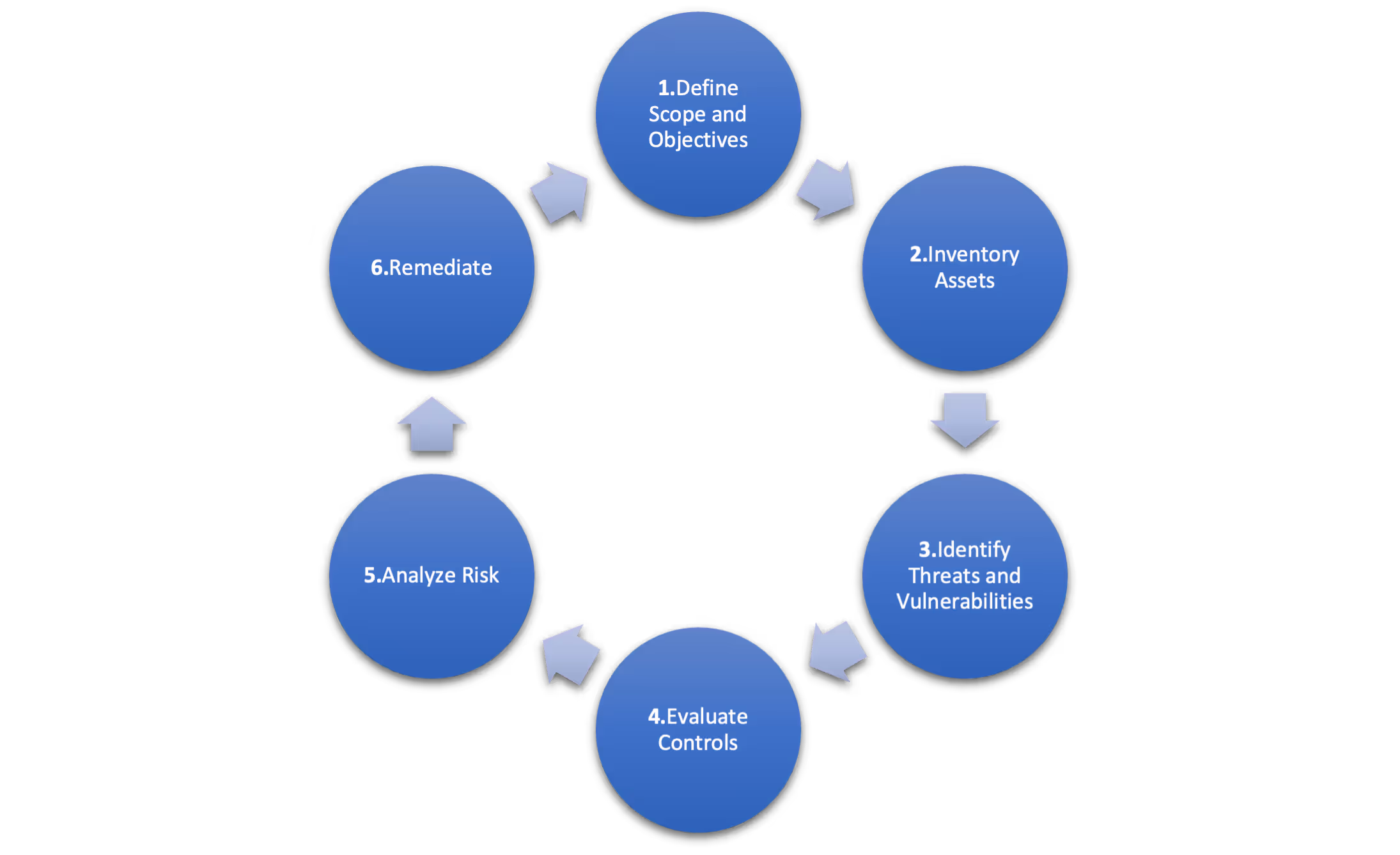
Steps Involved in a Cybersecurity Posture Assessment
- Define Scope and Objectives: The first step in conducting a cybersecurity posture assessment is to define the scope and objectives. This step involves identifying the systems, applications, and data that require evaluation. It is important to understand the business's criticality of each asset to prioritize the assessment's focus. As you consider scope, keep in mind the size of your team and the period of time you have for remediation. If this is a new practice for your organization, it may be prudent to focus on customer facing applications or critical services first. Consider what events would have the greatest impact to your business. These impacts may include fines due to noncompliance or lack of cyber liability insurance coverage. To aid in the selection of controls, consider alignment with a cybersecurity framework such as the CIS (Center for Internet Security) Top 18 controls, NIST Cyber Security Framework, or ISO27001:2022. Aligning to a framework assists by providing a list of best practices and context for what your program should look like.

- Inventory Assets: It’s hard to protect assets without an awareness of them. It’s important to have up to date accounting of hardware, software, and data assets as well as your 3rd party vendor relationships. An inventory is crucial for conducting a thorough assessment as it helps identify potential vulnerabilities in assets that may have been overlooked. Don’t let this step stop you from performing the assessment, many organizations have underdeveloped inventory capabilities, and it would be reasonable to identify this as a programmatic weakness to remediate.
- Identify Threats and Vulnerabilities: The third step in conducting a cybersecurity posture assessment is to identify potential threats and vulnerabilities. There are many ways to model threats using techniques such as the following:
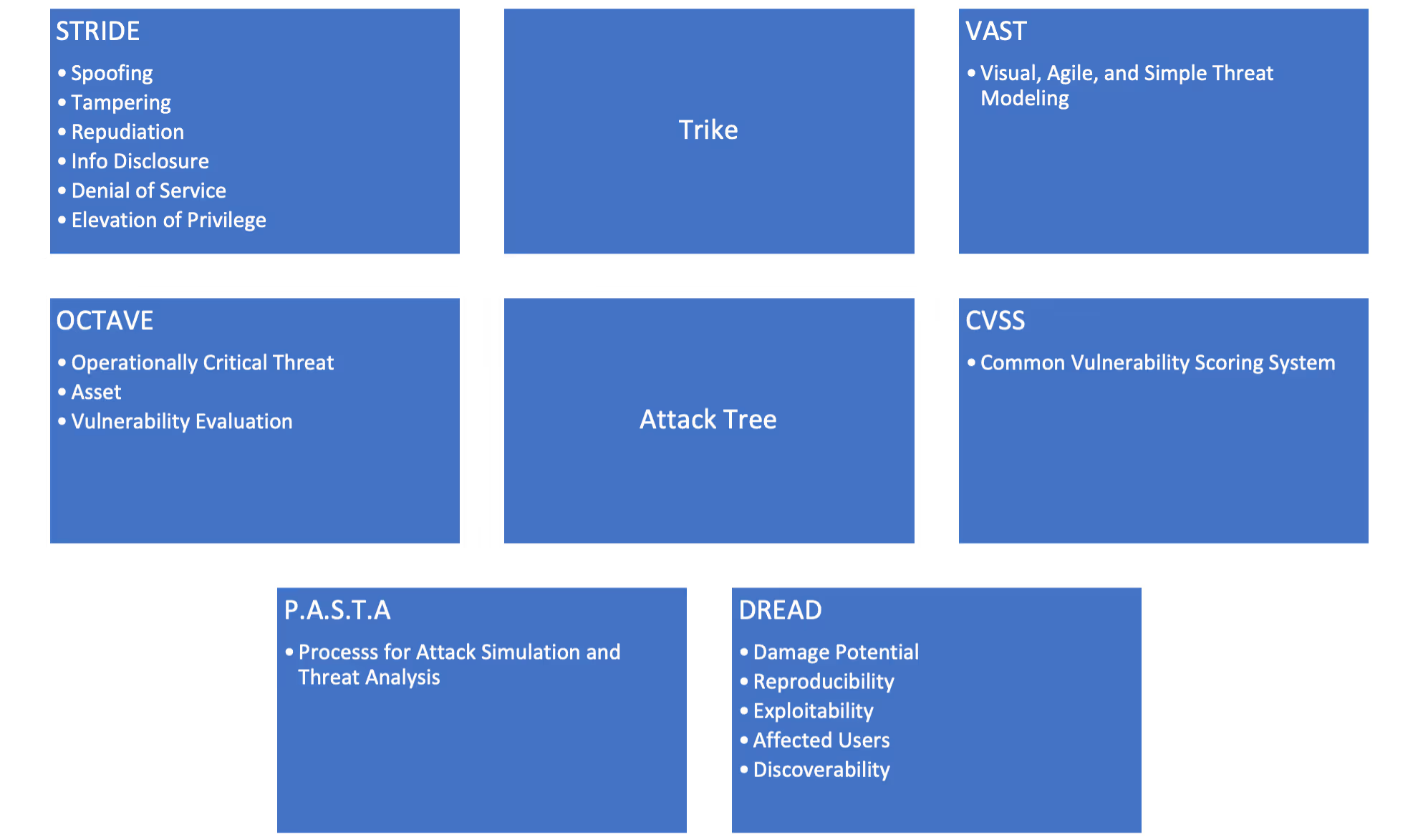
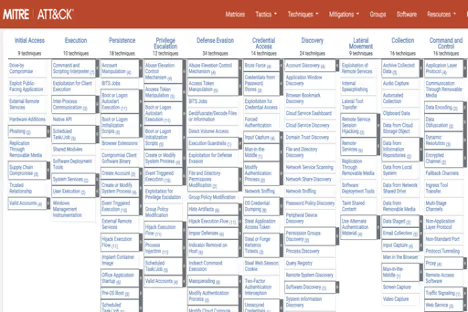
The Mitre ATT&CK framework is another resource to help identify threats and threat actor groups targeting your industry. This step involves conducting a comprehensive evaluation of the systems, applications, and data identified in the first two steps. The goal is to identify potential attack vectors and determine the severity of the identified risks. This can be conducted using internal resources through vulnerability scanning or through red teaming exercises (if your team has the skill set). As the skills required to properly emulate state of the art tactics, techniques and procedures often necessitate extensive training, many organizations elect to partner with security firms for vulnerability scans and penetration tests. These organizations can assist in building appropriate scope of work to align with your objectives and posture assessment scope.
- Evaluate Controls: The fourth step in conducting a cybersecurity posture assessment is to evaluate the effectiveness of the organization's security controls. This step involves assessing the current security measures implemented and determining whether they are effective in mitigating identified risks. This step is crucial in identifying gaps in the security posture that need to be addressed. The Mitre ATT&CK Framework can assist in mapping the identified vulnerabilities to mitigation techniques, while also providing context as to where in the threat actor’s campaign these vulnerabilities would be exploited.
- Analyze Risk: The fifth step in conducting a cybersecurity posture assessment is to analyze the identified risks. This step involves determining the likelihood and impact of each identified risk. This analysis helps prioritize the risks, and remediation activities can be assigned accordingly. Identified vulnerabilities are often accompanied by a severity rating (critical, high, medium, low, informational). As you review these consider how the severity of individual findings might be compounded when paired. For example: if 40% of your user population falls prey to a phishing campaign, multifactor authentication is not enforced, and the network is not segmented the aggregate risk is much greater than if you were to consider each weakness individually.
- Implement changes: The final step in this process is to organize the findings from the preceding steps and align resources to address them. It is important to track your efforts and approach to each risk (Transfer, Mitigate, Accept, Avoid). At this point in the process, you will have a better understanding of your cyber security posture on multiple levels such as weaknesses in process, policy, vulnerabilities in specific systems or lack of capabilities. It is crucial that your team is not discouraged or overwhelmed by the findings. Do your best to prioritize the findings based on severity and perceived impact. The important thing to do at this point is to act, keep the momentum, and improve at a sustainable pace.
Benefits of a Cybersecurity Posture Assessment
A cybersecurity posture assessment brings many benefits to an organization. It helps identify potential risks and vulnerabilities, which enables organizations to implement effective security controls to mitigate these risks. Conducting a cybersecurity posture assessment also helps organizations comply with industry standards and regulations. It also provides an opportunity to assess the organization's overall security posture and make informed decisions about investments in cybersecurity. This process will bring context to internal requests for resources and capabilities as well as measure the maturity of the organization’s cyber security program over time. This process may have ancillary benefits such as the following:

Conclusion
A cybersecurity posture assessment is a critical step in identifying potential threats and vulnerabilities to an organization's infrastructure. The assessment helps organizations prioritize and remediate identified risks, providing a roadmap to improve their cybersecurity posture. The six steps involved in a cybersecurity posture assessment are defining scope and objectives, inventorying assets, identifying threats and vulnerabilities, evaluating controls, analyzing risks, and implementing changes. The assessment is a critical tool for improving an organization's cybersecurity posture, making it more resilient to evolving cyber threats. Get started with a posture assessment today.













